CFPB Focuses on “Junk Fees” and a Slew of Issues in a Single Week

Junk Fee Initiative
October 28, 2022:
CFPB Focuses on “Junk Fees” and a Slew of Issues in a Single Week
 Earlier this week, the Consumer Financial Protection Bureau’s Rohit Chopra delivered a speech to the FDIC Board of Directors at the FDIC Advisory Committee on Economic Inclusion Meeting. During that presentation, Chopra commented:
Earlier this week, the Consumer Financial Protection Bureau’s Rohit Chopra delivered a speech to the FDIC Board of Directors at the FDIC Advisory Committee on Economic Inclusion Meeting. During that presentation, Chopra commented:
“CFPB will launch the first step of the rulemaking process on Personal Financial Data Rights, pursuant to a dormant authority under Section 1033 of the Consumer Financial Protection Act. The CFPB is developing proposals to require financial institutions offering deposit accounts, credit cards, digital wallets, prepaid cards, and other transaction accounts to set up secure methods, like APIs, for data sharing. By allowing individuals to share their personal financial data in a secure way, we can facilitate more switching, lower fees, and higher levels of customer care. In many respects, this will help us move toward more traditional, cash-flow underwriting and away from black-box models that use mysterious correlations and that invite concerns about bias. It can also reduce reliance on credit scores.”
Activities over the past week have more than emphasized the agency’s drive, including the following announcements,
- CFPB Kicks Off Personal Financial Data Rights Rulemaking
Proposals under consideration would fuel market competition and strengthen consumer data rights. CFPB outlined options to strengthen consumers’ access to, and control over, their financial data as a first step before issuing a proposed data rights rule that would implement section 1033 of the Dodd-Frank Act. Under the options the CFPB is considering, consumers would be able to more easily and safely walk away from companies offering bad products and poor service and move towards companies competing for their business with alternate or innovative products and services. - CFPB Takes Action to Address Junk Data in Credit Reports
CFPB) issued guidance to consumer reporting companies about their obligation to screen for and eliminate obviously false “junk data” from consumers’ credit reports. Companies need to take steps to reliably detect and remove inconsistent or impossible information from consumers’ credit profiles. For example, many children in foster care have large amounts of information on their credit reports that is clearly junk data because as minors they are prohibited from entering into most contracts for credit.
 Focusing on Guidance to Help Banks Avoid Charging Illegal Junk Fees on Deposit Accounts
Focusing on Guidance to Help Banks Avoid Charging Illegal Junk Fees on Deposit Accounts
Oct. 26, 2022 — The Consumer Financial Protection Bureau (CFPB) issued guidance about two junk fee practices that are likely unfair and unlawful under existing law. The first, surprise overdraft fees, includes overdraft fees charged when consumers had enough money in their account to cover a debit charge at the time the bank authorizes it. The second is the practice of indiscriminately charging depositor fees to every person who deposits a check that bounces. The penalty is an unexpected shock to depositors who thought they were increasing their funds.
“Americans are willing to pay for legitimate services at a competitive price, but are frustrated when they are hit with junk fees for unexpected or unwanted services that have no value to them,” said CFPB Director Rohit Chopra. “We are providing guidance on existing law that will help law-abiding businesses seeking to fairly compete and the families they serve.”
Overdraft and depositor fees likely violate the Consumer Financial Protection Act prohibition on unfair practices when consumers cannot reasonably avoid them. Today’s Consumer Financial Protection Circular on surprise overdraft fees and the CFPB’s compliance bulletin on surprise depositor fees lay out when a financial institution’s back-end penalties likely break the law.
Surprise Depositor Fees
When a consumer deposits a check that bounces, banks sometimes charge a fee to the depositor, usually in the range of $10 to $19. However, a person trying to deposit a check has no idea or control over whether the check will clear, and sometimes, that person is the victim of check fraud. In fact, there are many reasons deposited checks can bounce, and the most common reason is that the check originator does not have enough money available in their account. Charging a fee to the depositor penalizes the person who could not anticipate the check would bounce, while doing nothing to deter the originator from writing bad checks.
The bulletin explains that indiscriminately charging these depositor fees, regardless of circumstances, likely violates the Consumer Financial Protection Act. Financial institutions can generally stay on the right side of the law when they employ more tailored fee policies that charge depositor fees only in situations where a depositor could have avoided the fee, such as when a depositor repeatedly deposits bad checks from the same originator.
Surprise Overdraft Fees
An overdraft fee can become a surprise fee when the customer doesn’t reasonably expect their actions to incur an overdraft fee. For instance, even if a person closely monitors their account balances and carefully manages their spending to avoid overdraft fees, they can easily incur penalties when financial institutions employ processes that are unintelligible or manipulative.
Today’s Consumer Financial Protection Circular explains that when financial institutions charge surprise overdraft fees, sometimes as much as $36, they may be breaking the law. The circular provides some examples of potentially unlawful surprise overdraft fees, including charging penalties on purchases made with a positive balance. These overdraft fees occur when a bank displays that a customer has sufficient available funds to complete a debit card purchase at the time of the transaction, but the consumer is later charged an overdraft fee. Often, the financial institution relies on complex back-office practices to justify charging the fee. For instance, after the bank allows one debit card transaction when there is sufficient money in the account, it nonetheless charges a fee on that transaction later because of intervening transactions.
Related Reading:
- Consumer Financial Protection Circular, Surprise Overdraft Fee assessment practices
- CFPB Compliance Bulletin
- CFPB’s recent enforcement action against Regions Bank for charging surprise overdraft fees
- Learn about the CFPB’s work on junk fees at consumerfinance.gov/JunkFees.
In September 2022, the CFPB took action against Regions Bank for charging surprise overdraft fees known as authorized positive fees. As early as 2015 the CFPB, as well as other federal regulators, including the Federal Reserve, began cautioning financial institutions against charging certain types of authorized positive fees, such as the ones used by Regions to unlawfully penalize customers. Regions is required to, among other consequences, reimburse consumers all the funds it unlawfully charged since August 2018 and pay a $50 million penalty.
Today’s Consumer Financial Protection Circular on surprise overdraft fees and its bulletin on surprise deposited item fees are just the latest announcements as part of the CFPB’s junk fee initiative, one of many efforts across the federal government to increase competition and reduce unnecessary financial burdens on American families.
Junk Fee Initiative
In January 2022, the CFPB launched an initiative to scrutinize back-end junk fees that cost Americans billions of dollars. Tens of thousands of people responded to a CFPB Request for Information with their stories and complaints about unnecessary fees in banking. Since then, the CFPB has taken action to constrain “pay-to-pay” fees, and has announced a rulemaking proceeding on credit card late fees. In the last year, the CFPB has also published several research reports on overdraft fees and an analysis of college banking products.
The CFPB has observed that financial institutions have started to compete more when it comes to fees. Earlier this year multiple banks announced they were eliminating overdraft fees or updating their policies to be more consumer friendly. And, in recent months, multiple large banks announced that they are eliminating non-sufficient fund fees on their checking accounts. The CFPB estimates that these changes mean $3 billion in savings for consumers.
October 20, 2022:
The Future of Default Servicing
As fears of a recession grow, it would be prudent for everyone—servicers and regulators alike—to think hard about default servicing improvements and reforms.
Courtesy of Jonathan R. Kolodziej, DS News
 Oct. 2022 — More than two years after the COVID-19 pandemic took hold of the country, mortgage servicers may finally be in a position to come up for air and reflect on the whirlwind of the recent past. Among other things, the servicing industry has had to navigate the quick enactment of the CARES Act forbearance program, a constant barrage of agency and government-sponsored entity (GSE) guideline announcements and developments, a patchwork of state mandates, last-minute changes to the federal servicing rules in Regulation X, and intense public scrutiny from the Consumer Financial Protection Bureau (CFPB). To date, servicers have collectively provided assistance to many millions of mortgage loan borrowers who were impacted by the pandemic. While there is certainly still more work to be done, servicers’ willingness to help consumers and the overall effort put forth by the servicing industry at large has been admirable and commendable.
Oct. 2022 — More than two years after the COVID-19 pandemic took hold of the country, mortgage servicers may finally be in a position to come up for air and reflect on the whirlwind of the recent past. Among other things, the servicing industry has had to navigate the quick enactment of the CARES Act forbearance program, a constant barrage of agency and government-sponsored entity (GSE) guideline announcements and developments, a patchwork of state mandates, last-minute changes to the federal servicing rules in Regulation X, and intense public scrutiny from the Consumer Financial Protection Bureau (CFPB). To date, servicers have collectively provided assistance to many millions of mortgage loan borrowers who were impacted by the pandemic. While there is certainly still more work to be done, servicers’ willingness to help consumers and the overall effort put forth by the servicing industry at large has been admirable and commendable.
As the frequency and magnitude of COVID-related developments continues to slow down, now is a good time to reflect on the past couple of years and begin to plan for the future. What has worked well and could be incorporated into our standard servicing practices moving forward, and what lessons could be learned from mistakes that were made to improve the landscape for mortgage loan borrowers and their servicers in the future? Especially as fears of a recession grow, it would be prudent for everyone—servicers and regulators alike—to think hard about default servicing improvements and reforms.
Many industry groups and other interested parties have already been contemplating new forward-thinking policy ideas, such as putting more reliance on forbearance as a go-to option for consumers who are in the early stages of a financial hardship. However, there are also many legislative and regulatory reforms that should be considered as we move into a post-COVID world. This article outlines a few such ideas.
 WHERE WE’VE BEEN
WHERE WE’VE BEEN
Coming out of the financial crisis of the late 2000s, the Dodd-Frank Wall Street Reform and Consumer Protection Act of 2010 created the CFPB and instructed the new agency to implement reforms in the mortgage servicing industry. In 2013, the CFPB released its final mortgage servicing rules, and they became effective in January 2014. The new rules covered three main areas related to default servicing: (1) early intervention, which established an early and ongoing communication framework for borrowers who become delinquent; (2) continuity of contact, which attempts to ensure that servicers have dedicated personnel that are knowledgeable and able to assist delinquent borrowers; and (3) loss mitigation, which establishes a procedural framework for working with borrowers to find alternatives to foreclosure, as well as dual-tracking restrictions to ensure foreclosure and loss mitigation are not moving forward simultaneously.
In 2016, the CFPB released a substantial set of amendments to the original servicing rules, and a fair number of the changes were in the loss mitigation area. Since that time, the only movement has related to COVID. In June of 2020, the CFPB recognized the need to relax the existing loss mitigation restrictions to facilitate servicers’ ability to quickly and efficiently offer a deferral option to COVID-impacted borrowers. Finally, in July 2021, the CFPB released a COVID final rule that related exclusively to default servicing requirements in Regulation X. Among other things, the 2021 final rule imposed more prescriptive content requirements for many live contacts that are established with delinquent borrowers to ensure COVID options are discussed, it further loosened the loss mitigation restrictions to allow servicers to offer some streamlined loan modification options to borrowers that may have been impacted by COVID, and it instituted a strict prohibition on the filing of new foreclosure actions for the last few months of 2021, with only very limited exceptions.
WHERE WE’RE GOING
As we consider what the future of mortgage servicing should look like, we ought to acknowledge that, while there are many items that we might want to include on a theoretical wish list to improve servicers’ day-to-day lives, the practical reality is that any change in policy or in the regulatory environment must benefit consumers in a clearly articulable way. To have any meaningful chance of convincing the appropriate parties to make the recommended change, a proposal must not provide the industry with all the benefits, even if it is neutral for consumers; there must be some wins on the consumer side of the ledger.
With that in mind, one of the most obvious lessons that many learned from the pandemic was that streamlined loss mitigation options are a good thing and can be utilized to benefit servicers and borrowers alike. In early 2020, we saw that the CARES Act established a quick and efficient process for COVID-impacted borrowers to get immediate relief on their mortgage payments. The law created an extremely low bar for borrowers of federally backed mortgage loans to obtain up to 360 days of forbearance on their payments. Rather than having to submit mountains of documentation to demonstrate a possible hardship or evidence the borrower’s financial position, Congress mandated that servicers offer forbearance whenever it was requested provided that the borrower also attested to experiencing a COVID-related hardship. This could happen verbally, in writing, or even through a web portal or other online interface, making it extremely easy for borrowers to enter a forbearance program. Likewise, it also eliminated the need for servicers to expend the time and resources to work through a prolonged document chase process where they constantly try to obtain missing documentation that is needed to complete an application and for their review.
Shortly thereafter, the CFPB released its interim final rule to remove existing barriers in Regulation X that could have prevented servicers from quickly offering deferral options to COVID-impacted borrowers who were ready to resume making their regular monthly payment. A particular provision of Regulation X, which we commonly refer to as the “anti-evasion clause,” generally prohibits servicers from evaluating information received from a borrower and using it to offer loss mitigation options, unless and until the servicer collects a complete loss mitigation application from the borrower first. There are very limited exceptions to the anti-evasion clause including, for example, a carve-out for short-term forbearance plans, which allowed for the CARES Act framework to work seamlessly. Recognizing that its own rules were about to get in the way of helping millions of impacted mortgage loan borrowers, the CFPB issued an interim final rule to add COVID deferral options to the limited list of anti-evasion clause exceptions. Once again, this immensely benefited both consumers and servicers.
Finally, along the same lines as the 2020 interim final rule, the CFPB’s 2021 COVID final rule once again added a new exception to the anti-evasion clause in Regulation X, this time for certain streamlined modification options. At that time, the CFPB realized that the law accounted for, and allowed, forbearance and deferral options, but did not necessarily include a good way for servicers to quickly and efficiently evaluate borrowers who may need additional payment relief for a modification of the underlying loan. The result was another new exception to the anti-evasion clause, this time eliminating the barriers that otherwise would have stood in the way of quickly offering loan modification options to borrowers impacted by COVID–19, provided certain criteria are satisfied.
Click here to read and/or download the entire article.
October 14, 2022
Why The Crypto Economy Needs Stricter Anti-Fraud Protocols and Other Regulations
Related Reading:
-
- FSB Proposes Framework for the International Regulation of Crypto-Asset Activities Including Stablecoin Arrangements
- Regulation, Supervision and Oversight of Crypto-Asset Activities and Markets: Consultative Report
- Cryptos on the Rise 2022: A Complex Regulatory Future Emerges
- White House Urges Regulators to ‘Redouble’ Crypto Oversight Efforts
Courtesy of Tad Simons, Thomson Reuters Institute
 Oct. 11, 2022 — The use of digital or cryptocurrencies as a means of exchange has grown so large, so fast that both crypto-based businesses and mainstream financial institutions have reached a regulatory tipping point
Oct. 11, 2022 — The use of digital or cryptocurrencies as a means of exchange has grown so large, so fast that both crypto-based businesses and mainstream financial institutions have reached a regulatory tipping point
In order to assert their legitimacy and expand their market reach, cryptocurrency exchanges and crypto-based business platforms need access to mainstream financial institutions. In order for traditional banks and other institutions to feel comfortable doing business with crypto-based entities, those entities need to follow the same compliance rules as other financial institutions and businesses. At the very least, that means adhering to the same anti-money laundering (AML) protocols and customer due diligence (CDD) or know-your-customer (KYC) requirements as any other business.
Transparency and trust are the issues, and in the eyes of many detractors, the current digital-currency infrastructure doesn’t have enough of either.
The pros & cons of regulating crypto
Until recently, however, the whole idea of regulating the crypto market was considered antithetical to the ethos of anonymity and decentralization that made digital currencies so attractive in the first place. When Bitcoin was created in 2009, the whole point was to create a medium of exchange that operated outside the mainstream economic ecosystem of big banks and corporations.
Now, however, large factions in both the crypto industry and the mainstream financial community see stricter government regulation as necessary and beneficial. A better public-policy framework is the best way to create an economic infrastructure in which both digital currencies and traditional fiat currencies can co-exist, the argument goes. And this will help create the foundation of trust necessary for the cryptocurrency industry’s long-term viability.
However, the main part of the problem is that although most major crypto exchanges now require customers to provide at least some basic personal information (name, address, date of birth), many still do not. Further, most do not go to the trouble of establishing proof of life, such as by cross-comparing personal data with government databases and other publicly available information, or even establishing a risk score. There also isn’t an established method (or ethos) for sharing crypto customer information with authorities or law enforcement.
The other part of the problem? Like the casino industry in the 1990s, the crypto industry needs to rinse itself of the stink of crime. Crypto’s anonymity — once its biggest selling point — is now its greatest liability. Indeed, the ability to exchange money anonymously is precisely why cryptocurrencies are so popular with drug dealers, human traffickers, arms dealers, terrorists, money launderers, and other criminals. When ransomware hackers hold a business hostage, for example, there’s a reason they want to be paid in crypto.
Crypto-based criminal activity is also making it difficult for genuine crypto platforms to establish the legitimacy and trust that they desperately need in order to expand. Indeed, so many people dabbling in digital currencies have been scammed out of so much money recently that traditional financial institutions are understandably wary. According to the Federal Trade Commission, 46,000 people lost more than $1 billion to crypto scams between Q1 2021 and Q1 2022, and currently, crypto scams account for 40% of all dollars reported lost to fraud on social media.
Those in the pro-regulation camp argue that implementing more robust procedures for customer identity verification — such as CDD and KYC processes and AML requirements — would go a long way toward deterring the criminal element. This would also help establish the credibility and stability necessary for the crypto industry’s long-term viability.
Mainstream financial institutions want these same safeguards not only to mitigate risk and comply with the AML requirements listed in the existing Bank Secrecy Act (BSA), but to create a safe on-ramp to a potentially huge new market.
How regulators are cracking down
Moving from why the crypto industry needs more regulation to how it is to be done is the challenge lawmakers and financial regulators are grappling with at the moment.
There are many different types of so-called “virtual asset service providers,” after all, and new ones are being invented all the time. Beyond well-known cryptocurrency exchanges such as Binance, Kraken, and Coinbase, which is where most people purchase or trade digital assets; there are also stablecoin issuers, marketplaces for non-fungible tokens (NFTs), and decentralized finance (DeFi) protocols, the latter of which uses blockchain technology to create self-executing “smart contracts” that require no human intervention at all.
Setting up regulatory guardrails to keep up with the proliferation and popularity of all these digital assets has become a global challenge. At the moment, the United States is behind the European Union, United Kingdom, and some other countries in terms of enacting legislation to regulate digital assets, but the Biden administration is trying its best to catch up.
Currently, in the United States, cryptocurrency exchanges (though not other forms of digital assets) are supposed to be regulated under the BSA, but the law has yet to be amended to specifically apply to digital asset service providers, so enforcement has been spotty.
The new US framework
To fix that, the Biden White House recently released a framework for US crypto regulation based on six months of research and input from all relevant agencies and stakeholders, including the US Treasury, the Securities and Exchange Commission, and the Federal Reserve.
Dubbed the First-ever Comprehensive Framework for Responsible Development of Digital Assets, the document outlines a variety of policy recommendations that are meant to represent a “whole of government” approach to the regulation of all digital assets, including stablecoins and NFTs.
The framework addresses a wide variety of issues regarding consumer protections, national security concerns, environmental sustainability (mining cryptocurrencies requires a lot of electricity), and law enforcement. It also proposes avenues for international cooperation through such organizations as the Organization for Economic Co-Operation and Development and the Financial Stability Board. The framework even contains suggestions for how the Federal Reserve might release its own government-backed digital dollar, which Fed Chair Jerome Powell has said could eliminate the need for cryptocurrencies altogether, bringing the whole argument about digital assets full circle.
Nothing in the framework has been enacted into law yet, but it’s only a matter of time. Stricter regulation of the cryptocurrency market may be tearing away the cloak of anonymity that criminals and true believers cherish so much, but if the goal is to make all digital assets safer and more useful for everyone else then the cloak must be removed.
October 7, 2022
What Passes for ‘Big’ Is Getting Bigger: A Closer Look at CU Asset Size
Related Reading:
- Connexus Follows Other Credit Unions Over the $5 Billion Asset Mark
- The Two Main Drivers of Credit Union Asset Growth: High Interest Rates on Deposits And Marketing Expenses
- Largest CU-Bank Acquisition in Wisconsin History Is Complete: Meanwhile, Arizona Financial CU finalizes its acquisition of Horizon Community Bank
- From the Fed: The New Landscape for Banking Competition
Courtesy of Jim DuPlessis, Credit Union Times 
The large credit unions keep getting larger faster, making the definition of “large” an ever-moving target.
The NCUA has asset classes that are artifacts of statutes from the late 20th century, starting with an asset class of less than $10 million and moving up to the largest class of $500 million or more. As of June 30, credit unions with assets of less than $500 million accounted for 16% of the credit union movement’s assets.
Recently it has begun reporting results that use a $1 billion asset threshold for its largest group.
In early 2020, CU Times started using new thresholds based on the recognition that size is relative, and the relations change with time.
Three groups were devised with the intent that each have roughly the same assets in aggregate. But the thresholds were picked to be round, easily remembered numbers. The number of classes was three and named to conform to U.S. size standards for ordering soft drinks at a drive-thru: Small, medium and large.
Here was the breakdown as of Dec. 31, 2019:
- Small (less than $1 billion in assets) had collectively $510 billion in assets (32% the movement’s $1.58 trillion in assets as of December 2019) and 46.8 million members.
- Medium ($1 billion to less than $4 billion) had $517.3 billion in assets (33%) and 38.1 million members.
- Large ($4 billion or more) had $557.5 billion in assets (35%) and 36.8 million members.
Those thresholds were designed based on assets as of June 30, 2019, when the distribution was closer to 33% each. So credit unions that had $1 billion or less in assets were 34% of the movement’s total assets as of June 30, 2019, but that asset class had fallen to just 26% of total assets by June 30, 2022.
With the third quarter ending Friday, it seemed like as good a time as any to roll out new thresholds:
- Small (Less than $2 billion): These 4,727 credit unions had $827 billion in assets (38% of the total $2.16 trillion) and 56.8 million members as of June 30. This group’s assets have grown 20% since June 2020.
- Medium ($2 billion to less than $7 billion): These 188 credit unions had $637.8 billion in assets (30%) and 36.7 million members. Their assets have grown 24% in the past two years.
- Large ($7 billion or more): These 41 credit unions had $693.8 billion in assets (32%) and 40.3 million members. Their assets have grown 25% in the past two years.
The “small” asset class is now outsized, but past trends showed it is likely to shrink back towards 33%, while the big will get bigger.
As with past size definitions, earnings improve with size — whether using traditional annualized earnings as a percent of average assets (ROA), or operating ROA, which excludes the volatile, managed number of provisions for loan losses and instead substitutes it with net charge-offs.
Total credit unions’ ROA in the second quarter was 0.84%, down 32 bps from a year earlier, while operating ROA was 0.84%, down 17 bps. By size groups, earnings were:
- Small credit unions’ ROA in the second quarter was 0.68%, down 16 basis points from a year earlier, while operating ROA was 0.69%, down 9 bps.
- Medium credit unions’ ROA for medium-sized credit unions was 0.85%, down 35 bps from a year earlier, while operating ROA was 0.84%, down 28 bps.
- Large credit unions’ ROA in the second quarter was 1.03%, down 51 bps from a year earlier, while operating ROA was 1.03%, down 16 bps.
September 30, 2022
Expanding Crypto Lender Nexo Secures U.S. Banking Charter
A day after being sued by eight state attorneys general who claim it violated securities laws, crypto lender Nexo unveiled that it has purchased a stake in federally regulated Summit National Bank.
In buying a minority stake in the holding company that owns Summit National Bank, which is regulated by the Office of the Comptroller of the Currency, Nexo has substantially expanded the scope of products it can offer, notably bank accounts.
Other services include asset-backed loans, card programs, and escrow and custodial solutions through Summit National Bank, Nexo said in a release.
Related reading:
- U.S. State Regulators Charge Nexo Group For Not Registering Product
- Crypto Lender Nexo Stops Interest on New Deposits
- Getting Crypto Payments Compliance Right Requires Deep Experience
- Group of 9 Banks Pitches USDF Token as Stablecoin Alternative for Businesses
The deal will give its customers “access to some of the most innovative products at the intersection of traditional finance and blockchain technology,” said Kalin Metodiev, co-founder and managing partner of Nexo. He also joined the bank’s board. He also called it a major step “in Nexo’s relentless drive to better serve our U.S. customers in compliance with the constantly evolving regulatory landscape.”
Summit National Bank President and Chairman Forrest Gilman said the deal and addition of Metodiev to the board “strengthens our work on the transformation of the bank into a fully fledged cutting-edge FinTech bank with access to new clients.”
In addition the Summit partnership, Nexo plans to expand “its global commercial banking capabilities … by securing additional banking licenses on a global scale. It has more than 50 licenses and registrations globally, as well as an institutional custody solution and professional crypto trading platform.
Riding the Storm Out
Nexo has been pursuing an aggressive acquisition strategy after a series of bankruptcies by crypto lenders including Voyager Digital and Celsius spurred by the $48 billion collapse in May of a stablecoin, TerraUSD. That sent a major crypto hedge fund many crypto lenders had loaned heavily to, Three Arrows Capital, into insolvency, causing a domino effect.
In June, Nexo, which is based in Zug, the heart of Switzerland’s “Crypto Valley,” announced that it had hired Citigroup to advise it on acquisitions, taking advantage of a strong financial position while many of its competitors flailed with insolvencies or simply the crypto downturn.
Most notably, with the stated aim of strengthening its presence in Asia, Nexo is in talks to buy Singapore-based Vauld, one of the crypto lenders than halted withdrawals by customers who entrusted it with their crypto in exchange for interest.
That is the same financial product that led the attorneys general of New York, California and six other states to sue Nexo on Sept. 26.
That lawsuit follows on the $100 million settlement in February by BlockFi, a leading crypto lender, for selling unregistered securities in the form of those interest-bearing deposits with/investments in crypto lending. Half of that went to several dozen states and the rest to the Securities and Exchange Commission (SEC).
Buying Spree
Nexo is hardly the only company using that downturn to go shopping.
BlockFi became insolvent in the current crisis, but was rescued by FTX CEO Sam Bankman-Fried, who has been on an accelerating acquisition spree since before the crypto winter bear market began. And earlier this week, his U.S exchange, FTX US won a bidding war for Voyager Digital’s assets, suggesting Bankman-Fried is planning to push ahead with its own FTX Earn product.
Generally speaking, crypto lenders require borrowers to put up crypto worth 125% to 150% of the amount they want to borrow, getting loans in stablecoins. That collateral is automatically sold if volatile crypto prices drive it too close to the amount borrowed. While those loans, which normally in stablecoins, can be used for any purpose, most is used in risky decentralized finance, or DeFi, investments.
Nexo stopped accepting new U.S. clients. While it did not halt the service for existing clients, it stop paying interest on new deposits. Those changes would be in place “until the restructuring of the Earn Interest Product and the registration process with the relevant regulatory bodies are finalized,” it said at the time.
September 23, 2022
Data Protection as a Service
Per a recent article in TechCrunch, “Companies are facing hundreds of millions of dollars in fines these days for failing to comply with data protection and data privacy rules, and that’s driving wave of organizations, and their users, to get more serious about data protection.”
Related Reading:
- Data Protection As A Service (DPaaS) Global Market Report 2022
The data protection as a service (DPaaS) market research report is one of a series of new reports that provides market statistics, including DPaaS industry global market size, regional shares, competitors with market share, detailed market segments, trends and data. - Uber’s Hacker *Irritated* His Way Into Its Network, Stole Internal Documents
Employee was spammed so much with MFA requests that he could easily be tricked into accepting one. Then the hacker found a terrible blunder on the internal network. - American Airlines Says Data Breach Affected Some Customers, Employees
American Airlines Inc (AAL.O) on Tuesday confirmed a data breach and said while an “unauthorized actor” gained access to personal information of a small number of customers and employees through a phishing campaign, there was no evidence of data misuse.
Courtesy of GlobeNewsWire and ReportLinker
 The global data protection as a service (DPaaS) market is expected to grow from $17.88 billion in 2021 to $23.09 billion in 2022 at a compound annual growth rate (CAGR) of 29.1%. The data protection as a service (DPaaS) market is expected to grow to $63.38 billion in 2026 at a CAGR of 28.7%.
The global data protection as a service (DPaaS) market is expected to grow from $17.88 billion in 2021 to $23.09 billion in 2022 at a compound annual growth rate (CAGR) of 29.1%. The data protection as a service (DPaaS) market is expected to grow to $63.38 billion in 2026 at a CAGR of 28.7%.
The data protection as a service (DPaaS) market consists of sales of data protection as a service (DPaaS) by entities (organizations, sole traders, and partnerships) that are a collection of services that help organizations to protect their data and also improve their network security and recovery options.Data Protection-as-a-Service (DPaaS) is a cloud-based or web-based system for networking security and data loss prevention.
These services are provided to the clients through multiple memberships and help organizations in cutting the costs of system security and maintenance.
The main types of data protection as a service are disaster recovery as a service, backup as a service, and storage as a service.Disaster recovery as a service (DRaaS) is a cloud computing service model that enables an organization to back up its data and IT infrastructure in a third-party cloud computing environment and provides all DR orchestration, all through a SaaS solution, to regain access and functionality to IT infrastructure following a disaster.
Data protection as a service can be deployed in the public cloud, private cloud, and hybrid cloud in large enterprises and SMEs that can be used in various industries such as banking, financial services and insurance (BFSI), telecom & IT, government & public sector, healthcare, retail, energy & utilities, manufacturing, others.
North America was the largest region in the data protection as a service (DPaaS) market in 2021.Asia Pacific is expected to be the fastest-growing region in the forecast period.
The regions covered in the data protection as a service (DPaaS) market report are Asia-Pacific, Western Europe, Eastern Europe, North America, South America, Middle East, and Africa.
The increasing concern about data loss and data security is propelling the demand in the data protection as a service (DPaaS) market.Data loss refers to the loss of data due to internal issues like system failure or external issues like cyber attacks, etc.
Enterprises from all around the world have been concerned about data security recently due to incidents of data loss and data leaks.For instance, according to Identity Theft Resource Center’s report, a United States non-profit organization, the year 2021 saw 1,862 data breaches, which was up from 1,108 data breaches in 2020.
These breaches have increased concerns about data loss in companies. Hence, the increasing concerns about data loss and data security are driving the growth of the data protection as a service market.
New technological advancements like the integration of connected devices with the internet of things (IoT) and virtual private network (VPN) are shaping the data protection as a service (DPaaS) market.For instance, in May 2021, GLobal Electronic-SECurity (GLESEC), a cyber-security firm announced the launch of its new Orchestrated data leakage detection and protection service.
This security-as-a-service has a unique offering of detecting and protecting data leakage without the need to classify all the information of the company. With this service, the company would address the need for the organization’s security requirements.
In January 2021, Veritas, headquartered in California, a provider of enterprise data protection services, acquired HubStor for an undisclosed amount.With this acquisition, Veritas would add a SaaS-based data protection team to the team and would be able to bring data protection services to the cloud. Hubstor, headquartered in Canada, is data protection as a service provider. The countries covered in the data protection as a service (DPaaS) market report are Australia, Brazil, China, France, Germany, India, Indonesia, Japan, Russia, South Korea, UK, USA.
September 16, 2022
CFPB Study Details the Rapid Growth of “Buy Now, Pay Later” Lending
Business model relies on data collection, and loans serve as close substitute for credit cards
 Today, the Consumer Financial Protection Bureau (CFPB) published a report offering key insights on the Buy Now, Pay Later industry. The report, Buy Now, Pay Later: Market trends and consumer impacts , finds that industry grew rapidly during the pandemic, but borrowers may receive uneven disclosures and protections. The five firms surveyed in the report originated 180 million loans totaling over $24 billion in 2021, a near tenfold increase from 2019.
Today, the Consumer Financial Protection Bureau (CFPB) published a report offering key insights on the Buy Now, Pay Later industry. The report, Buy Now, Pay Later: Market trends and consumer impacts , finds that industry grew rapidly during the pandemic, but borrowers may receive uneven disclosures and protections. The five firms surveyed in the report originated 180 million loans totaling over $24 billion in 2021, a near tenfold increase from 2019.
“Buy Now, Pay Later is a rapidly growing type of loan that serves as a close substitute for credit cards,” said CFPB Director Rohit Chopra. “We will be working to ensure that borrowers have similar protections, regardless of whether they use a credit card or a Buy Now, Pay Later loan.”
Related Reading: Director Chopra’s Prepared Remarks on the Release of the CFPB’s Buy Now, Pay Later Report
Read the Report: Buy Now, Pay Later: Market trends and consumer impacts
Buy Now, Pay Later is a form of interest-free credit that allows a consumer to fully purchase a product, and then pay back the loan over four installments, with the first installment typically being a down payment on the purchase. Most Buy Now, Pay Later loans range from $50 to $1,000, and are subject to late fees if a borrower misses a payment.
 Buy Now, Pay Later rose to prominence in the past decade as an alternative form of credit for online retail purchases. The lending option has gained traction with consumers who seek the flexibility of being able to pay for goods and services over time, but who may have been leery of other credit products.
Buy Now, Pay Later rose to prominence in the past decade as an alternative form of credit for online retail purchases. The lending option has gained traction with consumers who seek the flexibility of being able to pay for goods and services over time, but who may have been leery of other credit products.
Once a niche financial offering that was heavily concentrated in apparel and beauty, Buy Now, Pay Later has now branched out to industries as disparate as travel, pet care, and even groceries and gas. Apparel and beauty merchants, who had combined to account for 80.1% of originations in 2019, only accounted for 58.6% of originations in 2021.
Other highlights of Buy Now, Pay Later loan usage include:
- Loan approval rates are rising: 73% of applicants were approved for credit in 2021, up from 69% in 2020.
- Late fees are becoming more common: 10.5% of unique users were charged at least one late fee in 2021, up from 7.8% in 2020.
- More purchases are ending in returns: 13.7% of individual loans in 2021 had at least some portion of the order that was returned, up from 12.2% in 2020.
- Lenders’ profit margins are shrinking: Margins in 2021 were 1.01% of the total amount of loan originated, down from 1.27% in 2020.
The marketing of Buy Now, Pay Later loans can make them appear to be a zero-risk credit option, but today’s report identified several areas of risk of consumer harm, including:
- Inconsistent consumer protections: Borrowers seeking Buy Now, Pay Later credit may encounter products that do not offer protections that are standard elsewhere in the consumer financial marketplace. These include a lack of standardized cost-of-credit disclosures, minimal dispute resolution rights, a forced opt-in to autopay, and companies that assess multiple late fees on the same missed payment.
- Data harvesting and monetization: Many Buy Now, Pay Later lenders are shifting their business models toward proprietary app usage, which allows them to build a valuable digital profile of each user’s shopping preferences and behavior. The practice of harvesting and monetizing consumer data across the payments and lending ecosystems may threaten consumers’ privacy, security, and autonomy. It also may lead to a consolidation of market power in the hands of a few large tech platforms who own the largest volume of consumer data, and reduce long-term innovation, choice, and price competition.
- Debt accumulation and overextension: Buy Now, Pay Later is engineered to encourage consumers to purchase more and borrow more. As a result, borrowers can easily end up taking out several loans within a short time frame at multiple lenders or Buy Now, Pay Later debts may have effects on other debts. Because most Buy Now, Pay Later lenders do not currently furnish data to the major credit reporting companies, both Buy Now, Pay Later and other lenders are unaware of the borrower’s current liabilities when making a decision to originate new loans.
Buy Now, Pay Later providers are subject to some federal and state oversight. The CFPB has enforcement authority over providers of credit, and it has authority to supervise any non-depository covered persons, such as a Buy Now, Pay Later provider, in certain circumstances. Some states consider Buy Now, Pay Later to be consumer credit and require state licensing or registration, as well as compliance with state consumer credit laws, while other states do not require licensing or registration for Buy Now, Pay Later products with no interest or finance charges.
To address the discrete consumer harms, the CFPB will identify potential interpretive guidance or rules to issue with the goal of ensuring that Buy Now, Pay Later lenders adhere to many of the baseline protections that Congress has already established for credit cards. As part of this review, the agency will also ensure Buy Now, Pay Later lenders, just like credit card companies, are subjected to appropriate supervisory examinations.
To address emerging risk issues with data harvesting, the CFPB will identify the data surveillance practices that Buy Now, Pay Later lenders should seek to avoid.
To reduce the risk of borrower overextension, the CFPB will continue to address how the industry can develop appropriate and accurate credit reporting practices. The agency will also take steps to ensure the methodology used by the CFPB and the rest of the Federal Reserve System to estimate household debt burden is rigorous.
Today’s report comes after the Bureau announced a market monitoring inquiry in December 2021 to gain more insight into the industry. In January 2022, the CFPB submitted a public notice and request for comments from the public on their experiences dealing with Buy Now, Pay Later loans. The data and insights in the report are based on feedback from that request, along with deidentified submissions in the public CFPB complaint database and publicly available financial filings and other source material from the five firms who received the Bureau’s market monitoring orders.
Consumers having an issue with a Buy Now, Pay Later product or service, or any other consumer financial product or service can submit a complaint with the CFPB online or by calling (855) 411-CFPB (2372).
September 9, 2022
The Cost of a Data Breach: Banking and Finance
Courtesy of Mark Stone, Security Intelligence
The importance of cybersecurity has touched almost every industry. Beyond that, robust cybersecurity is table stakes for several sectors, particularly health care and the banking and finance industry. Not only is financial data at risk, but so is customer trust. In banking and finance, trust means everything.
Yet, consumers are hesitant to share their confidential data. A recent McKinsey survey revealed that no industry achieved a trust rating of 50% for data protection. Here’s the most sobering stat: 87% of respondents said they’d refuse to do business with any company that they perceived as having weak security practices.
Related Reading
2022 Cost of a Data Breach Report: The average total cost of a data breach is $4.35 million, according to the new 2022 report from the Ponemon Institute. Explore cost factors, root causes and security best practices in this series.
KeyBank: Hackers of Third-Party Provider Stole Customer Data: Hackers stole personal data including Social Security numbers, addresses and account numbers of home mortgage holders at KeyBank, the bank reports, in the breach of a third-party vendor that serves multiple corporate clients.
Robinhood’s $20 Million Data Breach Settlement: The stock-trading app lacks “almost universal security measures,” according to a class action suit leading to the multi-million dollar payout.
Capital One to Pay Out $190M After Hacker Breached Millions of Customers’ Data: Capital One Financial Corp. has reached an agreement to pay $190 million to settle a class-action lawsuit that was filed after a hacker accessed personal information belonging to 100 million U.S. customers.
When banking and finance data breaches occur — and they do happen often — they don’t always stem from a bad actor. Often, breaches come from poorly secured third-party apps or a lack of proper user authentication protocols.
 Banking and Finance Data Breaches
Banking and Finance Data Breaches
Several data breaches struck these industries over the last year. What can we learn from them?
In January of 2021, attackers breached the accounts of three million Morgan Stanley corporate customers. The breach, reported in July, involved a third-party vendor. Attackers could access client names and addresses, social security numbers, date of birth and company names. The bank reported that attackers successfully exploited a vulnerability in the vendor’s server. Although the vulnerability was quickly patched, attackers still managed to obtain a decryption key for the encrypted files.
In December of 2021, crypto exchange Bitmart suffered a large-scale security breach. Attackers made away with $200 million worth of cryptocurrency. And all the bad actors had to do? Steal a single private key.
In November of 2021, online trading platform Robinhood announced a data security incident that affected millions of its customers. The company divulged that an “unauthorized third party” was able to obtain the email addresses of five million people and the full names of two million others. For 310 users, “additional personal information” was stolen. The attackers allegedly demanded a ransom payment following the breach.
How Much Does a Financial Breach Cost in 2022?
According to the 2022 IBM Cost of a Data Breach Report, the finance industry had the second highest average cost per breach, trailing only health care. While the average health care breach costs hit a new record high of $10.10 million (an increase of almost 42% since the 2020 report), financial organizations averaged $5.97 million per breach.
On a positive note, the Cost of a Data Breach report revealed that the average number of days to identify and contain a data breach fell from 287 in 2021 to 277 in 2022, a reduction of 10 days or 3.5%. The average number of days to contain a breach also fell in 2022 — from 75 days in 2021 to 70 days in 2022.
Risks and Challenges for Banking and Finance
Costly data breaches are only one side of the coin.
First, the industry must keep up with evolving digital transformation and technology innovations. Digital services, cloud computing and artificial intelligence (AI) play a key role. To meet customer demand, financial institutions must leverage more new applications, devices and infrastructure components. These, in turn, only increase their attack surface.
Next, banking and finance are subject to more complex regulations with each passing year. Data protection and privacy standards constantly change, and fines for non-compliance increase.
Third-party risk management is critical for any industry. However, banking and finance must be extra vigilant in ensuring vendors and third-party suppliers are secure. Third-party breaches underscore the financial services sector’s potential vulnerability to cyberattacks. After all, it increasingly relies on suppliers and vendors who cannot guarantee cybersecurity.
Finally, as the hybrid workplace gains popularity, so does an organization’s risk. Remote and hybrid work presents a more daunting challenge for industries with more critical data to protect.
Lowering Data Breach Costs
Although the threat landscape is expanding and breaches happen, proactive security measures work. The Cost of a Data Breach report shows how current security strategies can lower the average cost of a breach.
Security AI and Automation
Organizations that employ security automation like AI, machine learning, analytics and automated security orchestration saved on average $3.05 million per breach compared to firms using no security AI and automation.
Extended Detection and Response
2022 is the first time the report examined the effects of Extended Detection and Response (XDR) technologies on the cost of a data breach. Notably, organizations that deployed advanced threat detection and response tools averaged a savings of 9.2% per breach. While these savings may not seem significant, the true impact is realized in the reduction of breach duration — nearly one month.
Incident Response
Companies that have dedicated incident response (IR) teams and test their IR plan significantly reduced the average cost of a data breach by $2.66 million per breach compared to those with no IR team or no IR testing in place.
Risk Quantification
Risk quantification can highlight financial loss types by impact, loss of productivity, cost of response or recovery, reputation impact and fines and judgments. Companies using risk quantification saved $2.10 million per breach on average versus those that don’t.
Zero Trust
The zero trust approach assumes that user identities or the network itself may already be compromised. Instead, it relies on AI and analytics to continuously validate connections between users, data and resources. Not surprisingly, zero trust has a net positive impact on data breach costs, saving companies with a mature zero trust deployment $1.51 million on average per breach versus those with early adoption of zero trust.
These statistics provide the dose of optimism the industry needs. As more organizations invest in proactive security strategies and better cloud management practices, the impact and risk of a data breach can be reduced.
September 2, 2022 — Bank Secrecy Act: Action Needed to Improve DOJ Statistics on Use of Reports on Suspicious Financial Transactions
Courtesy of the U.S. Governmental Accountability Office
 Bank Secrecy Act (BSA) provisions for reporting suspicious financial transactions are intended to help law enforcement detect and investigate illicit finance activity. In GAO-19-582, Governmental Accountability Office (GAO) reported that financial institutions wanted more feedback on the usefulness of the BSA reports they file with Financial Crimes Enforcement Network (FinCEN).
Bank Secrecy Act (BSA) provisions for reporting suspicious financial transactions are intended to help law enforcement detect and investigate illicit finance activity. In GAO-19-582, Governmental Accountability Office (GAO) reported that financial institutions wanted more feedback on the usefulness of the BSA reports they file with Financial Crimes Enforcement Network (FinCEN).
The 2021 NDAA directs DOJ to annually report statistics on law enforcement agencies’ use of BSA reports, and directs FinCEN to provide additional feedback. The 2021 NDAA also contains a provision for GAO to report on practices that could improve BSA-related feedback. Among its objectives, this report examines steps DOJ and FinCEN have taken to implement these provisions.
GAO reviewed applicable laws, regulations, and agency documents, and interviewed officials from FinCEN, DOJ, other law enforcement agencies, and industry associations.
Fast Facts
Illegal financial activity can threaten safety and national security. Banks must report potentially illegal transactions to the Financial Crimes Enforcement Network (FinCEN), which makes the reports available to law enforcement agencies to help with investigations.
But law enforcement agencies usually don’t track data on the usefulness of these reports, so FinCEN can’t provide feedback to banks about the reports’ effectiveness.
To facilitate this feedback, the Department of Justice is required to provide information about the usefulness of these reports. But DOJ doesn’t collect adequate data to do so. Our recommendations address these issues.
Highlights: What GAO Found
The Financial Crimes Enforcement Network (FinCEN) is responsible for administering the Bank Secrecy Act (BSA), which requires financial institutions to file reports about suspicious financial transactions. FinCEN provides BSA report access to law enforcement agencies, which use those reports to support investigations. FinCEN receives limited data from law enforcement agencies on their use of BSA reports or the reports’ impact on case outcomes because agencies largely do not collect such data. As a result, FinCEN cannot provide comprehensive feedback to financial institutions on the usefulness of the BSA reports they file.
Feedback Loop for Bank Secrecy Act (BSA) Reporting
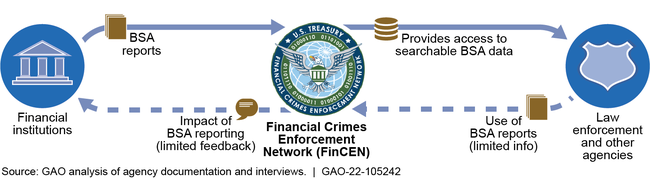
The 2021 National Defense Authorization Act (NDAA) directs the Department of Justice (DOJ) to provide annual statistics, metrics, and other information to the Secretary of the Treasury on agencies’ use of BSA reports, including how often reports contributed to arrests and convictions. But none of the agencies that DOJ contacted, including DOJ component agencies, provided the statistics described in the NDAA. DOJ’s first annual report focused on qualitative information and statistics already available to FinCEN. DOJ stated that agencies faced challenges collecting data that connect their use of BSA reports to case outcomes using current data systems.
DOJ has opportunities to leverage existing initiatives and expertise to improve its annual statistical report on agencies’ use of BSA reports.
- DOJ has been implementing a comprehensive, agency-wide data strategy to improve its data collection and infrastructure, but BSA-related data have not been included in the agencies’ efforts. Including these data would give DOJ an opportunity to examine how to improve its component agencies’ data collection on their use of BSA reports.
- DOJ’s first annual statistical report on BSA reflected some methodological weaknesses. For example, it did not include data from two agencies that track some uses of BSA reports because DOJ did not have procedures for following up on its data requests. The DOJ office that drafted the report did not collaborate with DOJ’s Chief Information Officer or Statistical Official in the report’s design. By involving the expertise of these DOJ offices in the development of future annual reports, DOJ could better ensure a rigorous methodology for collecting and presenting the report’s required statistics.
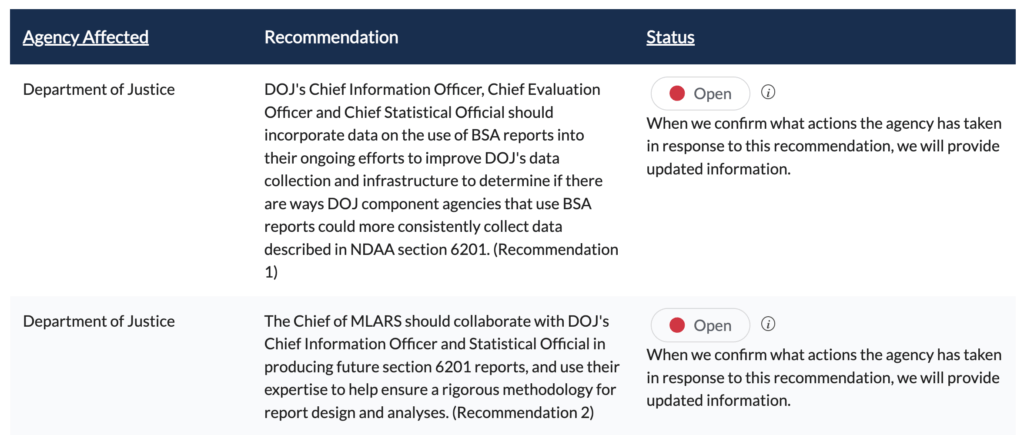
Recommendations
GAO recommends that DOJ (1) include data on the use of BSA reports in its ongoing agency-wide efforts to improve data collection, and (2) involve its Chief Information Officer and Statistical Official, in the design of its annual BSA statistical report. DOJ neither agreed nor disagreed with the recommendations.
Recommendations for Executive Action
Report’s Conclusions
FinCEN has made some progress in providing more feedback to institutions that file BSA reports, and its planned domestic liaison office is a step in improving feedback further. But FinCEN’s ability to provide feedback on the impact of BSA reports is limited because it depends on other agencies tracking their use of BSA reports, and agencies face challenges linking BSA reports to outcomes.
Thus, facilitating data collection on the use of BSA reports is a necessary first step to providing comprehensive feedback on the value of BSA reporting. By including data on the use of BSA reports in its ongoing efforts to build capacity for data collection, DOJ may identify data system improvements and other ways for its component agencies that use BSA reports to track their use. While DOJ component agencies are not the only users of BSA data, they represent a substantial portion of such users and could demonstrate best practices for effectively tracking the use of BSA reports to other agencies.
Beyond the need for additional data collection, the value of DOJ’s first annual report on the impact of BSA reports was limited because it lacked some available data and reflected some methodological weaknesses. By leveraging the expertise of DOJ data offices in the development of future summary reports, the agency could help ensure a rigorous methodology is used for collecting and presenting the report’s required statistics and also improve the quality of the information it provides to FinCEN. By taking both these steps, DOJ ultimately could improve the feedback FinCEN gives to filing institutions on the use and usefulness of their BSA reporting.
August 26, 2022 Feature: 57th Annual State System Summit
![]() Attendees can click here to access presentations and more.
Attendees can click here to access presentations and more.
(Event registration and MFA required.)
Hosted in sunny Huntington Beach, CA, the 57th Annual State System Summit (S3) brought together more than 100 industry leaders, including state and federal regulators, credit union CEOs, industry leaders, and experts, to share best practices and collaborate on industry issues.
Welcome to California
One of the benefits of attending the National Association of State Credit Union Supervisors (NASCUS) S3 is the ability to network and collaborate with credit union industry professionals from across the country to exchange ideas and resources. NASCUS President and CEO Brian Knight opened the event, introducing NASCUS Board Chairs Rose Conner and Mike Williams to welcome attendees and speak about the vitality of the state system.
 California’s own Diana Dykstra, President/CEO of CA/NV Credit Union Leagues, warmed up the crowd and highlighted the innovations and history of the credit union system within the state.
California’s own Diana Dykstra, President/CEO of CA/NV Credit Union Leagues, warmed up the crowd and highlighted the innovations and history of the credit union system within the state.
“Here in California, the very first credit union was established in 1921…a postal credit union…Today, we have 296 with $281 billion in total assets, 13 million members, and 1631 branches…I’m proud to be a NASCUS member and long-time supporter. What you do is extremely important. Collaboration, innovation, and improving the charter is what you do best.”
 Senior Deputy Commissioner, Department of Oversight, California Department of Financial Protection & Innovation (DFPI), Ed Gill, emphasized his agency’s continuous growth and evolution.
Senior Deputy Commissioner, Department of Oversight, California Department of Financial Protection & Innovation (DFPI), Ed Gill, emphasized his agency’s continuous growth and evolution.
“We’ve recently seen our authority expanded throughout through statute. We now oversee debt collectors and student loan services…non-bank small business lenders, fintech companies, debt relief companies, consumer credit reporting agencies, and other covered persons…Furthermore. Gov Governor Gavin Newsom recently issued an executive order directing a multi-agency approach to develop effective oversight of blockchain and crypto assets.”
![]() Click here to view the 2022 State System Summit Photo Album
Click here to view the 2022 State System Summit Photo Album
Hot Topics: Evolving Technologies and Threats
 In a world of “crypto-curious” entities, the global financial system needs to define rapidly evolving technologies, determine safe parameters, and map out best practices. As a result, NASCUS hosted a panel discussion on the variables surrounding Distributed Ledger Technology (DLT) moderated by Chelsea Treboniak, Owner of Critical Ops, with a panel of industry experts, including the Honorable Kyle Hauptman, Vice Chairman of the NCUA, Becky Reed, CEO of Lone Star Credit Union, and John Wingate, CEO of BankSocial.
In a world of “crypto-curious” entities, the global financial system needs to define rapidly evolving technologies, determine safe parameters, and map out best practices. As a result, NASCUS hosted a panel discussion on the variables surrounding Distributed Ledger Technology (DLT) moderated by Chelsea Treboniak, Owner of Critical Ops, with a panel of industry experts, including the Honorable Kyle Hauptman, Vice Chairman of the NCUA, Becky Reed, CEO of Lone Star Credit Union, and John Wingate, CEO of BankSocial.
DLT serves as a record of consensus with a cryptographic audit chain validated by nodes. With blockchain functioning as a variant of DLT and cryptocurrency as an encrypted data string that denotes a unit of currency, this panel openly analyzed the links and differences surrounding these evolving components.
“The real game changer here is distributed ledger technology, where you’re taking what we used to do with databases and decentralized data services. And now distributing it, you get more resilience across the system, you get more transparency across the system…distributed ledger is the real game changer here, not blockchain,” commented John Wingate.
This panel discussion incorporated audience-based questions and engagements touching on topics such as state-based crypto working groups, Central Bank Digital Currency development, potential Federal Reserve actions, smart contracts, and more.
Immediately following the DLT session, attendees participated in a series of roundtable activities on cybersecurity. In this session, participants worked side-by-side with peers to “think like the bad actors” and troubleshoot opportunities to mitigate vulnerabilities in various scenarios, including fraud, cybersecurity, and automated processes.
Special Guests and Celebrations
 Each year, NASCUS celebrates an individual and their career-long efforts with the Pierre Jay Award. This award acknowledges a career of “proven service, commitment, and leadership to NASCUS and the state-charter system.” That honor was bestowed to former Connecticut Financial Institutions Division Director Mary Ellen O’Neill this year.
Each year, NASCUS celebrates an individual and their career-long efforts with the Pierre Jay Award. This award acknowledges a career of “proven service, commitment, and leadership to NASCUS and the state-charter system.” That honor was bestowed to former Connecticut Financial Institutions Division Director Mary Ellen O’Neill this year.
“On behalf of the NASCUS leadership and staff, I want to congratulate Mary Ellen on her achievement. This award honors her considerable impact on the health and well-being of the state system,” commented Brian Knight, President and CEO of NASCUS. “She has dedicated her career to ensuring a safe, sound, and robust dual charter system, and we are deeply grateful for her friendship and contributions throughout her career.”
 In addition to celebrating state system accomplishments, NASCUS is investing in the future. Each year, the National Association of Credit Union Service Organizations (NACUSO) hosts a “Big Idea” Competition illustrating “innovation and drive for advancements within the industry.” In April, Illuma Labs and Posh Technologies won the honor of being this year’s Big Idea. The end product integrated the Illuma Shield™ passive voice authentication solution with conversational AI IVR from Posh to securely enable credit union members to access their accounts by voice recognition verification.
In addition to celebrating state system accomplishments, NASCUS is investing in the future. Each year, the National Association of Credit Union Service Organizations (NACUSO) hosts a “Big Idea” Competition illustrating “innovation and drive for advancements within the industry.” In April, Illuma Labs and Posh Technologies won the honor of being this year’s Big Idea. The end product integrated the Illuma Shield™ passive voice authentication solution with conversational AI IVR from Posh to securely enable credit union members to access their accounts by voice recognition verification.
“I had the pleasure of presenting alongside Karan Kashyap at the NASCUS S3 event on how Illuma and Posh Technologies are collaborating to provide enhanced member experience and security at credit union contact centers through the graceful fusion of our AI and voice authentication technologies. Thank you, NASCUS, for having us at the event and for all the insightful questions from the attendees,” said Milind Borkar, Founder/CEO of Illuma.
During the Annual Meeting, NASCUS announced new officers and newly elected and appointed directors to the NASCUS Regulator Board and Credit Union Advisory Council.
- Oregon Division of Financial Regulation’s Janet Powell was elected to the position of Board Chair on the Regulator Board (3-year term)
- Washington Department of Financial Institutions’ Amy Hunter was elected to the position of Director on the Regulator Board (3-year term)
- North Dakota Department of Financial Institutions’ Corey Krebs was appointed to the position of Director on the Regulator Board (1-year term)
- Southeast Financial Credit Union’s Jeff Dahlstrom (TN) was elected to the position of Credit Union Advisory Council Chair (3-year term)
- VyStar Credit Union’s Brian Wolfburg (FL) was elected to the position of Credit Union Advisory Council Vice-Chair (3-year term)
- TruMark Financial Credit Union’s Rick Stipa (PA) was elected to the position of Credit Union Advisory Council Director (3-year term)
- Metro Credit Union’s Robert Cashman (MA) was appointed to the position of Credit Union Advisory Council Director (1-year term)
Strategies for the Future
 Over the course of three pack-filled days, NASCUS guests participated in a series of networking activities, learning opportunities, and position-specific problem-solving meetings. State regulators met in an afternoon of segmented meetings to discuss inter-agency topics, best practices, and commonalities between states. Credit unions and Credit Union Leagues participated in specialized sessions covering issues such as strategy development with Filene Institute’s Mark Meyer and Fraud Schemes with Frank Drake from Smith Debnam Narron Drake Saintsing & Myers, LLP.
Over the course of three pack-filled days, NASCUS guests participated in a series of networking activities, learning opportunities, and position-specific problem-solving meetings. State regulators met in an afternoon of segmented meetings to discuss inter-agency topics, best practices, and commonalities between states. Credit unions and Credit Union Leagues participated in specialized sessions covering issues such as strategy development with Filene Institute’s Mark Meyer and Fraud Schemes with Frank Drake from Smith Debnam Narron Drake Saintsing & Myers, LLP.
Throughout the week, attendees enjoyed deep dives into topics with experts such as:
- Dr. Robert Eyler’s (Interim Associate Vice President of Government Relations and Professor of Economics at Sonoma State University) presentation on recent economic forecasts and national trends in terms of recovery, housing markets, interest rates, and inflation and the effects on members nationwide;
- Steven Jung’s (Vice President/Regional Sales Director, Federal Reserve Bank of Chicago) introduction to FedNow and the enablement of instant payments;
- Bryan Mogensen’s (Principal, CLA [CliftonLarsonAllen LLP]) perspective on the challenges facing the credit unions system with a continued focus on strategic and operational planning, new growth opportunities, CECL, the war on talent, and more;
Looking Ahead
 As we move into the future, attendees noted sensitivities to other potential issues, including data protection, complications with AI technologies such as multi-lingual necessities and authentication, synthetic identity fraud, and more. The event emphasized the idea that technology is driving innovation, collaboration, and conversation.
As we move into the future, attendees noted sensitivities to other potential issues, including data protection, complications with AI technologies such as multi-lingual necessities and authentication, synthetic identity fraud, and more. The event emphasized the idea that technology is driving innovation, collaboration, and conversation.
Events like these are essential to the state system, providing a stage for discovery, extensive issue remediation, and collaboration. NASCUS wants to thank this year’s event sponsors for making this event possible,

In 2023, NASCUS will host the 58th Annual State System Summit in Nashville, TN.
Last but not least, NASCUS invites you to join us for other topic-specific educational and networking events, such as our Director’s Colleges, Industry Day, Examiner Schools, the 2023 Cannabis Symposium, and more. Bookmark the NASCUS Education and Events page to stay up-to-date on current offerings.
August 12, 2022 OPINION: The Trip Back to Reality Starts: Mortgages, HELOCs, Delinquencies, and Foreclosures in Q2
Forbearance and pandemic cash run out. But a lot of fun was had by all.
Courtesy of Wolf Richter, WolfStreet.com
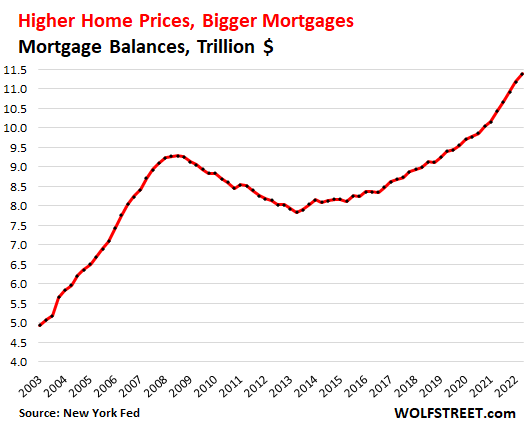
August 5, 2022 — Mortgage balances jumped by 9% in Q2 from a year ago, as prices spiked year-over-year, while people bought far fewer homes – sales of existing homes dropped by 10% from Q2 last year, and sales of new single-family houses plunged by 19% over the same period.
Mortgage balances have surged relentlessly since the end of the Housing Bust in 2012. Over those 10 years, mortgage balances surged by $4.6 trillion, and over the past three years, mortgage balances surged by $2.0 trillion, or by 21%, to $11.4 trillion, according to data from the New York Fed’s Household Debt and Credit Report.
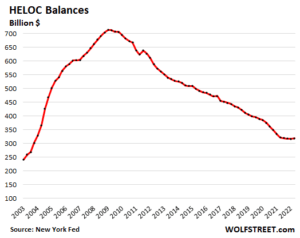
HELOCs end long decline.
Home Equity Lines of Credit fell out of favor after 2009 and balances declined steadily, unwinding the massive surge of the years before the Financial Crisis. As the Fed’s interest-rate repression and QE pushed down mortgage rates, and as home prices rose, folks began to cash-out-refinance their mortgages to generate cash, rather than drawing on HELOCs.
But now the decline has ended. HELOC balances ticked up in Q2 to $319 billion, from the low in the prior quarter. This has occurred as mortgage rates have spiked, and as cash-out refis have plunged.
There is now a new dynamic in place: Much higher mortgage rates: It would be stupid to refinance a 3% mortgage with a 5% mortgage in order to draw $100,000 in cash out of the home. It’s better to leave the 3% mortgage alone, and get a $100,000 HELOC that charges 5% on the outstanding balance, if any. So I expect HELOC balances to rise further going forward because the cash-out refi game has changed.
Mortgages are by far the biggest part of consumer debt, bigger than ever.
Nothing comes even close. Consumer debt balances in Q2:
-
- Mortgages: $11.4 trillion
- Student loans: $1.6 trillion
- Auto loans: $1.5 trillion
- Credit cards: $890 billion
- “Other” (personal loans, etc.): $470 billion
- HELOCs: $320 billion.
Mortgages is where the big systemic risks used to be due to the sheer size of the market and the high leverage.
But now, commercial Banks in the US only hold about $2.4 trillion of residential mortgages, including HELOCs, on their balance sheets, and those are spread among 4,300 commercial banks. Thousands of Credit Unions and other lenders also hold some mortgages on their balance sheets.
But most mortgages are now securitized into mortgage-backed securities. MBS fall into two categories:
- Most are government-backed MBS. Here the taxpayer is on the hook, not investors and lenders.
- A smaller portion of MBS are “private label” – not backed by government entities. They’re held by global bond funds, pension funds, insurance companies, etc.
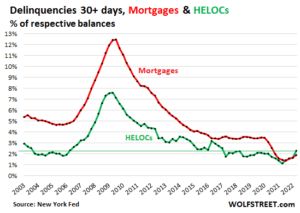
Delinquencies start trip back to reality. A lot of fun was had by all.
Under the pandemic-era forbearance programs, homeowners that fell behind on their mortgage payments, or stopped making mortgage payments altogether, and then entered into a forbearance program, were reclassified to “current” instead of delinquent. They didn’t have to make mortgage payments, and could use the cash saved from those not-made mortgage payments for other stuff. Eventually, they would have to work out a deal with the lender to exit the forbearance program.
The spike in home prices since spring 2020 allowed homeowners, when it came time to exit the forbearance program, to either sell the home and pay off the mortgage and walk away with extra cash; or work out a deal with the lender, such as a modified mortgage with a longer term, a lower rate, and lower payments. And a lot of fun was had by all.
But with forbearance programs over, mortgage delinquencies started to rise this year from the record lows last year.
Mortgage balances that were 30 days or more delinquent rose to 1.9% of total mortgage balances in Q2, up from 1.7% in Q1. It was the third quarter-to-quarter increase in a row, from the record low in Q2 2021. But it remains below all pre-pandemic low points (red line).
HELOC balances that were 30 days or more delinquent rose to 2.3% of total HELOC balances, the fourth quarter-to-quarter increase in a row, from the record low in Q2 2021. They’re now higher than they were before the Housing Bust (green line).
The HELOC delinquency rate in Q2 was higher than the mortgage delinquency rate for the first time ever, which makes you go hmmm.
Foreclosures rose, but are still near record lows.
The number of consumers with foreclosures rose to 35,120 borrowers, up from 24,240 in Q1 and up from the record low range of 8,100 to 9,600 last year.
Foreclosures are still far below any of the prior lows before the pandemic. At the low point in Q2 2005, during the Best of Times just before the Housing Bust took off, there were 148,780 foreclosures, over four times as many as now.
By comparison, during the three-year time span from 2008 through 2011, the peak of the mortgage crisis, over 400,000 consumers per quarter had foreclosures, including 566,180 at the peak in Q2 2009.
During the Best of Times before the Housing Bust, around 150,000 consumers had foreclosures; and during the Good Times before the pandemic, about 75,000 consumers had foreclosures per quarter. This range from 75,000 to 150,000 foreclosures might represent something like the old Good Times Normal (blue box), and we’re still not there yet:
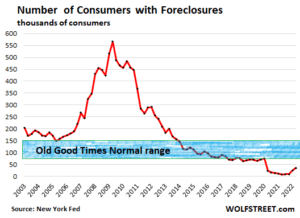
Home prices and foreclosures.
A surge in foreclosures cannot happen unless there is a plunge in home prices. When a homeowner who’d bought the home two years ago for $400,000 gets in trouble now, when the home price has jumped by 25% to $500,000, they can just sell the home, pay off the mortgage, pay the fees, and walk away with left-over cash. And there won’t be a foreclosure.
If the price of that house drops 25% eventually to $375,000, and the borrower owes $390,000 on the mortgage, that exit is getting tougher.
If the price plunges by 40% to $300,000, the easy exit is closed. That’s when foreclosures are starting to happen in large numbers, especially if they’re accompanied by a large-scale surge in unemployment, and that’s what happened during the Mortgage Crisis. But that’s not on the table just yet.
August 5, 2022 Feature: Buying To Get Big: US Credit Unions Push for Bank Acquisitions
Credit union leaders say the strategy delivers growth and protects community services – but they face opposition and legal challenges from the banking lobby.
Courtesy of Miles Hadfield, COOP News
 August 1, 2022 — With turbulent economic forces piling pressure on small financial institutions, consolidation is a growing trend in the US financial services sector. This has brought many mergers between credit unions – and another outcome is the record number of purchases of banks by credit unions.
August 1, 2022 — With turbulent economic forces piling pressure on small financial institutions, consolidation is a growing trend in the US financial services sector. This has brought many mergers between credit unions – and another outcome is the record number of purchases of banks by credit unions.
The emphasis is still on consolidation within the sector: the National Credit Union Administration (NCUA) says there have been 900 mergers from 2016 to 2020. But S&P Global figures show that 13 banks were acquired by credit unions in 2021, and industry observers such as Michael Bell, finance expert at Detroit law firm Honigman, expects at least 25 more such deals this year.
“My prediction is based on the work and deal flow I am seeing,” he told American Banker. “I spend most of my time working on these deals, and I have never seen so much activity.”
Bank purchases are a strategy highlighted by US credit union representatives at the recent Association of British Credit Unions (Abcul) conference. Eric Broome, from Georgia’s Own Credit Union, told delegates that mergers, acquisitions and private partnerships are a valuable mechanism for US credit unions to grow the scale and the raise capital they need to keep up with digitisation and increasingly competitive markets.
Related: Full reports from the World Credit Union Conference 2022
He said his credit union has already bought one small single-site bank and is preparing to buy another, as part of a strategy that includes developing a crypto-currency option, partnerships with fintechs, developing holding companies and sharing back office functions with other credit unions.
But it is important to plan things properly and find the right bank to buy, he warned. “You have to have a strategy. You can’t just do it willy nilly … you have to assess strengths and weaknesses to find the right partners, and make sure it’s a collaborative process.”
Other examples from the sector include acquisitions by GreenState Credit Union of North Liberty, Iowa, of four banks in 2020 and 2021, and two bank purchases by Orlando, Florida’s Fairwinds Credit Union – moves which, the credit unions say, deliver new product lines, expanded memberships, asset growth, efficiency and infrastructure such as ATM networks.
This trend has prompted howls of protest from the US banking sector – which already has its knives sharpened for credit unions over their tax-exempt status. Credit union apex bodies such as the National Association for Federally Insured Credit Unions (Nafcu) have been defending this for several years against an aggressive campaign from the banking lobby.
Banks have been bringing legal challenges to individual credit union acquisitions, with tussles in Nebraska, Colorado, Iowa and Tennessee – where a court battle is raging over a proposed purchase by Orion Federal Credit Union of Memphis-based Financial Federal Bank, which has assets of US$818m (£683m).
In November 2021, Davidson County Chancery Court Judge Patricia Moskal placed an injunction on the deal, while she assessed the implications of the Tennessee Banking Act. At the end of May, Moskal lifted this, ruling that the act allowed the purchase because the credit union is acquiring the bank’s assets, not its charter or stock.
But the state regulator, the Tennessee Department of Financial Institutions (TDFI), which opposes the deal, has struck back, filing an appeal at the end of June to overturn the ruling.
Moskal, in her ruling, said the TDFI has approved similar transactions when the acquirer was a state-chartered or out-of-state bank. “The legislature could have included a limitation on the types of entities permitted to purchase the assets of a state-chartered bank, but it did not do so,” she wrote. But submitting his appeal against Moskal’s ruling on 14 June, TDFI Commissioner Greg Gonzales argued that Financial Federal account holders would be “irreparably harmed and disrupted” by the deal, along with the state’s banking system.
The Tennessee Bankers Association is also hostile to the deal. In a blog post, its president/CEO Colin Barrett wrote: “Unfortunately these deals have been on the rise around the country in recent years.” He said Financial Federal is “a strong, well respected Memphis bank” while Orion, which “began as a small credit union whose mission was to serve teachers in Memphis” had used “its tax advantaged status and weak regulatory oversight to grow to a position where it can acquire a $750m bank”.
Barrett accused Orion of abandoning its “desire to serve people of modest means” with a move that would turn it into a near $2bn financial institution. “Bank acquisitions by credit unions have fuelled passionate discussions by the TBA board over recent years,” he added. “There is debate about whether these acquisitions should be prohibited in statute, even if they already are. And there is discussion around what can be done at the state and local level to rein in credit unions.
“But whatever we do on the state level will continue to pale in comparison to the work that needs to be done in Congress. Whether it is credit unions buying banks, expanding their business lending or opening their membership to anyone who can fog a mirror, the part I find most frustrating is the blind eye turned by members of Congress.”
NAFCU has been among the credit union bodies working to fend off such attacks from the banking sector. In a briefing note, it says: “Mergers between credit unions and community banks are not new and have occurred over the last decade as the rate of financial institution consolidation has increased.
“Overwhelming compliance burdens and costs since financial crisis and enactment of the Dodd-Frank Act have made it harder to survive as a community bank or credit union. This has caused financial industry consolidation, which has led to fewer and fewer merger options.”
It says regulatory relief for community institutions would help slow the consolidation trend, adding that mergers between banks and credit unions “represent a tiny percentage of overall mergers in the financial services sector”.
These mergers are “typically a win-win”, argues NAFCU: while credit unions get to expand, local people see the protection of community-focused financial services, local jobs and branches, which might be lost through a sale to a national bank. “Credit union-community bank mergers often mean employees retain jobs and branches remain open with a focus on the members in the community,” it argues.
“Big banks, on the other hand, are focused on profits and making money from a merger. A look at the financial health of community banks that have recently merged with credit unions shows that those institutions are generally less-profitable, and thus less attractive, as potential merger partners for larger for-profit banks.”
But the road to mergers remains rocky. As well as opposition from the banking sector, hurdles include the time it can take to complete a deal.
And regulator the National Credit Union Administration caps business loan rates for credit unions at 12.25% which is a bar against buying a bank with a large commercial portfolio. Credit unions also face regulatory questions over how bank customers fit into their field of membership, if carried over as members.
One example which shows the challenges that face the sector is recent attempt by Jacksonville, Florida-based VStar Credit Union to merge with Georgia community bank Heritage Southeast which was – called off in June after the boards of both organisations decided there was no “clear path forward to obtaining the regulatory approvals needed for closing”.
July 29, 2022 Feature: A Busy Week at the CFPB
The Consumer Financial Protection Bureau, led by Rohit Chopra, aims to “protect consumers from unfair, deceptive, or abusive practices and take action against companies that break the law.” Activities in the past week have more than emphasized this mission, including,
- Fining U.S. Bank $37.5 Million for Illegally Exploiting Personal Data to Open Sham Accounts for Unsuspecting Customers
- Penalizing Trident Mortgage Company (Berkshire Hathaway Subsidiary) $22 Million for Deliberate Discrimination Against Minority Families in tandem with the DOJ
- Publishing Analysis of Potential Impacts of Medical Debt Credit Reporting Changes
- Ordering Hyundai to Pay $19 Million for Widespread Credit Reporting Failures
- Issuing New Debt Collection FAQs
Fines U.S. Bank $37.5 Million for Illegally Exploiting Personal Data to Open Sham Accounts for Unsuspecting Customers
 The bank pressured employees to sell, leading them to access credit reports and open accounts without permission.
The bank pressured employees to sell, leading them to access credit reports and open accounts without permission.
The CFPB took action against U.S. Bank for illegally accessing its customers’ credit reports and opening checking and savings accounts, credit cards, and lines of credit without customers’ permission. U.S. Bank pressured and incentivized its employees to sell multiple products and services to its customers, including imposing sales goals as part of their employees’ job requirements. In response, U.S. Bank employees unlawfully accessed customers’ credit reports and sensitive personal data to apply for and open unauthorized accounts. U.S. Bank must make harmed customers whole and pay a $37.5 million penalty.
The CFPB’s investigation found specific evidence that revealed that U.S. Bank was aware that sales pressure was leading employees to open accounts without authorization, and the bank had inadequate procedures to prevent and detect these accounts. Specifically, U.S. Bank imposed sales goals on bank employees as part of their job requirements. U.S. Bank also implemented sales campaigns and an incentive-compensation program that financially rewarded employees for selling bank products.
U.S. Bank’s conduct harmed its customers in the form of unwanted accounts, negative effects on their credit profiles, and the loss of control over personally identifiable information. Customers also had to waste time and energy closing unauthorized accounts and resolving consequences stemming from them, including seeking refunds for improperly charged fees.
The CFPB found that U.S. Bank violated the Consumer Financial Protection Act, the Fair Credit Reporting Act, the Truth in Lending Act, and the Truth in Savings Act. Specifically, U.S. Bank was:
- Exploiting personal data without authorization: The Fair Credit Reporting Act, among other things, defines the permissible uses of credit reports, and users of credit reports may only request them if they have a permissible purpose. U.S. Bank used customers’ credit reports without a permissible purpose, and without its customers’ permission, to facilitate opening unauthorized credit cards and lines of credit.
- Opening accounts without consumer permission: U.S. Bank opened deposit accounts, credit cards, and lines of credit without permission. This included opening Reserve and Premier lines of credit, which carry high interest rates and expensive fees. This behavior violated the Consumer Financial Protection Act and the Truth in Lending Act.
- Failing to provide legally required consumer disclosures: The Truth in Savings Act requires banks to provide certain disclosures when opening new deposit accounts. U.S. Bank violated the law when its employees opened consumer deposit accounts without permission and, in the process of doing so, failed to provide the required disclosures.
CFPB/DOJ Order Trident Mortgage Company (Berkshire Hathaway Subsidiary) to Pay More Than $22 Million for Deliberate Discrimination Against Minority Families
 Settlement is the first government resolution involving illegal redlining by a nonbank mortgage lender.
Settlement is the first government resolution involving illegal redlining by a nonbank mortgage lender.
The CFPB and U.S. Department of Justice (DOJ) took action to end Trident Mortgage Company’s intentional discrimination against families living in majority-minority neighborhoods in the greater Philadelphia area. The CFPB and DOJ allege Trident redlined majority-minority neighborhoods through its marketing, sales, and hiring actions. Specifically, Trident’s actions discouraged prospective applicants from applying for mortgage and refinance loans in the greater Philadelphia area’s majority-minority neighborhoods. If entered by the court, the settlement, among other things, would require Trident to pay a $4 million civil penalty to the CFPB to use for the CFPB’s victims’ relief fund. The Attorneys General of Pennsylvania, New Jersey, and Delaware also finalized concurrent actions.
Trident’s discriminatory actions, alleged by the CFPB and the DOJ, violated the Equal Credit Opportunity Act and the Consumer Financial Protection Act. The DOJ also alleged a violation of the Fair Housing Act. Specifically, the government’s investigation uncovered a wide range of problematic conduct by Trident, such as:
- Distributing racist language and messages about certain neighborhoods: Trident’s loan officers, assistants, and other employees received and distributed e-mails containing racial slurs and racist content. In addition to using racist tropes and terms, communications sent on work e-mails included pejorative content specifically related to real estate properties’ locations and appraisals. The racist content also targeted the people living in majority-minority neighborhoods.
- Avoiding sending its loan officers to market to majority-minority neighborhoods: Trident’s loan officers worked out of 53 different offices in the Philadelphia MSA, the locations of which were displayed on Trident’s website. Fifty-one of those offices were in majority-white neighborhoods. The other two offices were in neighborhoods with minority groups representing roughly 50% of the population. All 23 offices within the Philadelphia and Camden metropolitan areas that were within Trident’s lending area were in majority-white neighborhoods.
- Developing marketing campaigns and advertisements that discouraged and ignored minority mortgage loan applicants: For example, between 2015 and May 2018, Trident conducted 15 direct mail marketing campaigns. All the individuals pictured in the campaigns’ marketing materials—both models and Trident employees—appeared to be white. These direct mail marketing campaigns would have discouraged applicants from majority-minority neighborhoods. Additionally, Trident targeted its marketing materials to majority-white neighborhoods. Trident’s open house flyers, for instance, were overwhelmingly concentrated in majority-white neighborhoods, and its online advertisements appeared for home listings overwhelmingly located in majority-white neighborhoods.
Publishes Analysis of Potential Impacts of Medical Debt Credit Reporting Changes
 Removing Paid Collections Will Have Limited Benefit Across Consumer Groups.
Removing Paid Collections Will Have Limited Benefit Across Consumer Groups.
The CFPB published an analysis of how actions announced by the three largest national consumer reporting companies – Experian, Equifax, and TransUnion – will affect people who have allegedly unpaid medical debt on their credit reports. Nearly half of those with medical collections appearing on their credit reports will continue to see them there even after the changes fully go into effect next year. The medical collection tradelines that will remain on credit reports after the changes will likely represent a majority of the dollar amount of all medical collections currently reported.
The report finds the changes likely will result in the majority of individual medical collections tradelines being removed from credit reports. However, in terms of dollar amount, a large majority of reported medical collections likely will still remain. The report also highlights the characteristics of consumers with reported medical collections currently, and provides a state-by-state breakout of how the credit reporting changes will impact consumers’ credit reports.
Among other findings from today’s report:
- Two-thirds of medical collections on credit reports will no longer be reported. Starting in 2023, medical collections tradelines less than $500 will no longer be reported on consumer credit reports. Medical bills under $500 are significantly more likely to remain on a credit report for longer than medical bills over $500. For patients and families who have only relatively small outstanding medical bills, the $500 threshold could mean a large reduction in coercive credit reporting.
- Announced changes will likely have varied geographic impact. Patients and families living in states in the north and east of the U.S. have higher concentrations of medical debt that are paid. Residents of these states also have higher concentrations of medical debt with lower balances. As a result, people living in the north and east are more likely to benefit from the national credit reporting companies’ announcement. West Virginians appear particularly well-situated to benefit, with more than 80% of medical collections associated with consumers in West Virginia likely to be removed.
- Certain groups will receive less relief. Although residents of lower income, majority Black or Hispanic census tracts are more likely to have medical collections tradelines on their credit reports than residents of high income and majority white census tracts, they are slightly less likely to benefit from the announced changes by having all their medical collections tradelines removed.
Orders Hyundai to Pay $19 Million for Widespread Credit Reporting Failures
 Company Furnished Inaccurate Account Information to Credit Reporting Companies, Including Wrongly Reporting that Consumers were Delinquent on Loans or Leases.
Company Furnished Inaccurate Account Information to Credit Reporting Companies, Including Wrongly Reporting that Consumers were Delinquent on Loans or Leases.
The CFPB penalized Hyundai Capital America (Hyundai) for repeatedly providing inaccurate information to nationwide credit reporting companies and failing to take proper measures to address inaccurate information once it was identified between 2016 and 2020. The CFPB found that Hyundai used manual and outdated systems, processes, and procedures to furnish credit reporting information—which led to widespread inaccuracies—and resulted in negative inaccurate information being placed on consumers’ credit reports through no fault of their own. In total, the CFPB found that Hyundai furnished inaccurate information in more than 8.7 million instances on more than 2.2 million consumer accounts during that period. The order requires Hyundai to take steps to prevent future violations and to pay more than $19 million, including $13.2 million in redress to affected consumers who were inaccurately reported as delinquent and a $6 million civil money penalty, making this the CFPB’s largest Fair Credit Reporting Act case against an auto servicer.
Between January 2016 and March 2020, the CFPB also found Hyundai violated the Fair Credit Reporting Act (FCRA) and its implementing regulation, Regulation V, by:
- Failing to report complete and accurate loan and lease account information: Hyundai repeatedly did not take steps to promptly update and correct information it furnished to credit reporting companies that it determined was not complete or accurate, and continued to furnish this inaccurate and incomplete information.
- Failing to provide date of first delinquency information when required: FCRA requires data furnishers to provide credit reporting companies the date of delinquency for when a delinquent account is being charged off or placed for collections. Hyundai failed to report a date of delinquency for many consumers who were more than 90 days delinquent.
- Failing to modify or delete information when required: Hyundai’s furnishing system often overrode manual corrections made by employees in responding to consumer disputes. The furnishing system would provide monthly updates to credit reporting companies that reintroduced the data error after it had been disputed and corrected.
- Failing to have reasonable identity theft procedures: FCRA requires furnishers to respond to any notifications from credit reporting companies about furnished information that is the result of identity theft. Hyundai failed to establish reasonable identity theft and related blocking procedures to respond to identity theft notifications, and continued to report such information that should have been blocked on a consumer’s report.
- Failing to have reasonable accuracy and integrity policies and procedures: Regulation V requires furnishers to maintain written policies and procedures regarding the accuracy and integrity of the information furnished. Hyundai failed to review and update its credit reporting furnishing policies and procedures from 2010 to 2017. It was not until 2021 that the company finally updated some of its credit reporting policies and procedures.
CFPB Issues New Debt Collection FAQs

The questions and answers below pertain to compliance with the Debt Collection Rule.
This is a Compliance Aid issued by the Consumer Financial Protection Bureau. The Bureau published a Policy Statement on Compliance Aids, available here, that explains the Bureau’s approach to Compliance Aids.
Topics
- Limited-Content Messages
- Telephone Call Frequency
- Telephone Call Frequency: Presumptions
- Telephone Call Frequency: Excluded Calls
- Telephone Call Frequency: Rebutting the Presumptions
- Validation Information
- Validation Information: Residential Mortgage Debt
- Prohibitions on Third-Party Communications
- Electronic Communication
- Electronic Communication: Opt-out Notice
- Unusual or Inconvenient Times or Places
July 22, 2022 Feature:
Georgia State University Reports The Next Big Financial Crisis Could Be Triggered by Climate Change – But Central Banks Can Prevent It
Authored by
- Garth Heutel, Associate Professor of Economics, Georgia State University
- Givi Melkadze, Assistant Professor of Economics, Georgia State University
- Stefano Carattini, Assistant Professor in Economics, Georgia State University
 In 2008, as big banks began failing across Wall Street and the housing and stock markets crashed, the nation saw how crucial financial regulation is for economic stability – and how quickly the consequences can cascade through the economy when regulators are asleep at the wheel. Today, there’s another looming economic risk: climate change. Once again, how much it harms economies will depend a lot on how financial regulators and central banks react.
In 2008, as big banks began failing across Wall Street and the housing and stock markets crashed, the nation saw how crucial financial regulation is for economic stability – and how quickly the consequences can cascade through the economy when regulators are asleep at the wheel. Today, there’s another looming economic risk: climate change. Once again, how much it harms economies will depend a lot on how financial regulators and central banks react.
Climate change’s impact on economies isn’t always obvious. Mark Carney, the former governor of the Bank of England, identified a series of climate change-related risks in 2015 that could shake the financial system. The rising costs of extreme weather, lawsuits against companies that have contributed to climate change and the falling value of fossil fuel assets could all have an impact.
Nobel Prize-winning U.S. economist Joseph Stiglitz agrees. In a recent interview, he argued that the impact of a sharp rise in carbon prices – which governments charge companies for emitting climate-warming greenhouse gases – could trigger another financial crisis, this time starting with the fossil fuel industry, its suppliers and the banks that finance them, which could spill over into the broader economy.
Our research as environmental economists and macroeconomists confirms that both the effects of climate change and some of the policies necessary to stop it could have important implications for financial stability, if preemptive measures are not undertaken. Public policies addressing, after years of delay, the fossil fuel emissions that are driving climate change could devalue energy companies and cause investments held by banks and pension funds to tank, as would abrupt changes in consumer habits.
The good news is that regulators have the ability to address these risks and clear the way to safely implement ambitious climate policy.
Climate-stress-testing banks
First, regulators can require banks to publicly disclose their risks from climate change and stress-test their ability to manage change. The Biden administration recently introduced an executive order on climate-related financial risk, with the goal of encouraging U.S. companies to evaluate and publicly disclose their exposure to climate change and to future climate policies.
In the United Kingdom, large companies already have to disclose their carbon footprints, and the U.K. is pushing to have all major economies follow its lead. The European Commission also proposed new rules for companies to report on climate and sustainability in their investment decisions across a broad swath of industries in its new Sustainable Finance Strategy released on July 6, 2021. This strategy builds on a previous plan for sustainable growth from 2018.
Carbon disclosure represents a crucial ingredient for “climate stress tests,” evaluations that gauge how well-prepared banks are for potential shocks from climate change or from climate policy. For example, a recent study by the Bank of England determined that banks were unprepared for a carbon price of US$150 per ton, which it determined would be necessary by the end of the decade to meet the international Paris climate agreement’s goals.
The European Central Bank is conducting stress tests to assess the resilience of its economy to climate risks. In the United States, the Federal Reserve recently established the Financial Stability Climate Committee with similar objectives in mind.
Monetary and financial policy solutions
Central banks and academics have also proposed several ways to address climate change through monetary policy and financial regulation. One of these methods is “green quantitative easing,” which, like quantitative easing used during the recovery from the 2008 recession, involves the central bank buying financial assets to inject money into the economy. In this case, it would buy only assets that are “green,” or environmentally responsible. Green quantitative easing could potentially encourage investment in climate-friendly projects and technologies such as renewable energy, though researchers have suggested that the effects might be short-lived.
A second policy proposal is to modify existing regulations to recognize the risks that climate change poses to banks. Banks are usually subject to minimum capital requirements to ensure banking sector stability and mitigate the risk of financial crises. This means that banks must hold some minimum amount of liquid capital in order to lend.
Incorporating environmental factors in these requirements could improve banks’ resilience to climate-related financial risks. For instance, a “brown-penalizing factor” would require higher capital requirements on loans extended to carbon-intensive industries, discouraging banks from lending to such industries. Broadly, these existing proposals have in common the goal of reducing economy-wide carbon emissions and simultaneously reducing the financial system’s exposure to carbon-intensive sectors.
The Bank of Japan announced a new climate strategy on July 16, 2021, that includes offering no-interest loans to banks lending to environmentally friendly projects, supporting green bonds and encouraging banks to disclosure their climate risk. The Federal Reserve has begun to study these policies, and it has created a panel focused on developing a climate stress test.
Lessons from economists
Often, policymaking trails scientific and economic debates and advancements. With financial regulation of climate risks, however, it is arguably the other way around. Central banks and governments are proposing new policy tools that have not been studied for very long. A few research papers released within the last year provide a number of important insights that can help guide central banks and regulators.
They do not all reach the same conclusions, but a general consensus seems to be that financial regulation can help address large-scale economic risks that abruptly introducing a climate policy might create. One paper found that if the climate policy is implemented gradually, the economic risks can be small and financial regulation can manage them.
Financial regulation can also help accelerate the transition to a cleaner economy, research shows. One example is subsidizing lending to climate-friendly industries while taxing lending to polluting industries. But financial regulation alone will not be enough to effectively address climate change.
Central banks will have roles to play as countries try to manage climate change going forward. In particular, prudent financial regulation can help prevent barriers to the kind of aggressive policies that will be necessary to slow climate change and protect the environments our economies were built for.
July 15, 2022 Feature: 26 Eye-Opening Data Breach Statistics in 2022
Related Reading:
- 6 Potential Long-Term Impacts of a Data Breach: A data breach can destroy a business. For small- and medium-sized businesses (SMB), this is really especially concerning, as 60% will shut down within six months of the attack. While larger companies and agencies likely won’t have to shut their doors, they, too, suffer serious consequences. There are financial costs, which Ponemon Institute and IBM determined average $4.24 million, with 38% of that total coming from lost business. The hit to a company’s reputation after a breach takes its toll; consumers want to conduct business at companies that they deem safe. At least, they want to conduct business with those capable of keeping attackers away from their personal data.
- More Than 150 Banks, CUs Hit by ‘Brand Impersonation Attacks’ in Q1, Analysis Finds
- Microsoft Patch Tuesday: 86 Flaws, Four Critical, One Being Used in Attacks
- Top 10 Biggest Data Breaches of All Time
Courtesy of Catherine Reed, Firewall Times
 Billions of people have had their data compromised – in a single data breach, no less. In this article, we’ll dig into some key statistics on data breaches, digging into impact, cost, attack vectors, and more.
Billions of people have had their data compromised – in a single data breach, no less. In this article, we’ll dig into some key statistics on data breaches, digging into impact, cost, attack vectors, and more.
Data Breach Impact Statistics
1. 45% of U.S. Companies Experienced a Data Breach in 2021
While the size of the incidents varied, approximately 45% of U.S. companies experienced some form of a data breach, according to a 2021 report. While that figure is concerning, it’s lower than the 65% figure recorded in 2019. [Source: Thales Group]
2. 294 Million People Were Impacted by Data Breaches in 2021
While data breaches are still prevalent, the number of people impacted actually declined by 5% in 2021. That brought the total number of affected people down to about 294 million. In some cases, that may seem like positive news. However, it mainly represents a shift in attacker mentality, with many starting to favor focused hacks over large-scale data theft. [Source: CNET]
3. Over 15 Years, the U.S. Had More Than 12,000 Breaches Involving Over 11.1 Billion Records
Between 2005 and mid-2020, there were approximately 12,098 reported data breaches. In total, those incidents represented 11.1 billion compromised records [Source: Comparitech]
4. Russia Saw the Biggest Increase in Data Breaches in Q1 2022
Likely spurred by the war in Ukraine, Russia has become a target for data breach attempts. During Q1 2022, approximately 3.5 million internet users were impacted. Overall, it resulted in an 11% increase in data breach activity quarter-to-quarter. [Source: Surfshark]
5. With 3 Billion Compromised Accounts, the 2013 Yahoo Breach Was the Biggest Data Breach of All Time
When it comes to wide-scale data breaches, the 2013 Yahoo breach was the largest by far. Overall, a shocking 3 billion accounts were compromised. The event was also a costly one. The settlement alone was $117.5 million – to say nothing of additional damages, such as the hit to Yahoo’s reputation and the cost of shoring up their security. [Source: CNN & Reuters]
6. On Average, It Takes 287 Days to Discover a Data Breach
While most would hope it occurred faster, the average amount of time it takes to detect a data breach is a surprising 287 days. That’s just a bit more than 9 ½ months. [Source: IBM]
7. It Takes an Average of 80 Days to Contain a Breach
Once a data breach is detected, that doesn’t mean it’s immediately addressable. Instead, it takes an average of 80 days to get everything contained. That means it takes about one full year to identify that a breach occurred and get the situation remotely under control. [Source: IBM]
Data Breach Attacker Statistics
8. Over 75% of Data Breaches Are Perpetrated by Organized Crime Groups
When it comes to attackers, most aren’t single individuals looking to harm a company. Instead, more than 75% of data breaches are perpetrated by organized crime groups. This can include state-backed hacking agencies or coordinated private hacker groups. [Source: Verizon]
9. Russia Responsible for More Than Half of All State-Backed Hacking Activity
On the state-backed hacking front, Russia is more active than any other country. The nation represents more than half of state-backed attacks. [Source: Microsoft]
10. Success Rate of State-Backed Russian Hacking Attempts Rises from 21% to 32%
Along with being the most prevalent state-backed hacking force, Russia is increasingly successful in its attempts. In 2020, its success rate was estimated at 21%. In 2021, that rate rose to 32%. [Source: Microsoft]
11. 85% of Data Breaches Involve a Human Element
While it’s easy to assume that brute force plays a role in most data breaches, that isn’t the case. Instead, 85% involve a human element. For example, social engineering, lost credentials, clicking on malicious links, or other human-related missteps or vectors are more often involved than simple forced entry into a system. [Source: Verizon]
12. 25% of Data Breaches Involve Phishing
Phishing is currently the most popular attack vector for data breaches. Overall, phishing is involved in approximately 25% of all data breach incidents. [Source: Verizon]
13. 33% of IT Professionals Saw an Increase in Phishing Via Non-Email Platforms
While email remains the dominant channel for phishing, attackers are increasingly phishing via alternate avenues. Overall, 33% of IT professionals saw an increase in non-email phishing attempts in 2021. Among them, 44% saw phishing attempts on video conferencing platforms, and 40% experienced them on workforce messaging solutions. 40% also saw them on cloud-based sharing platforms, while 36% experienced text messaging-based phishing. [Source: Ironscales]
14. Ransomware Attacks Increase to 22% of All Breach-Related Cyberattack Activity
Ransomware attacks have been on the rise in recent years. In 2021, 22% of data breaches involved ransomware. Additionally, experts believe that the strategy will ultimately surpass phishing, potentially as early as this year. [Source: CNET]
15. 60% of Data Breaches Involve Insider Threats
While many attribute data breaches to outside forces – like hackers – insider threats are actually responsible for 60% of incidents. However, the harm isn’t always intentional, and risky behavior or human error can have unintentional consequences that result in a breach. [Source: idwatchdog by Equifax]
16. One in Five Breaches Happen Due to Lost or Stolen Credentials
Lost or stolen credentials are a popular way for attackers to gain entry into systems. Overall, about one-in-five companies that experienced a malicious breach in 2021 was compromised because lost or stolen credentials were involved. [Source: IBM]
17. Marriott/Starwood Breach the Largest Data Breach of All Time Involving a State-Sponsored Attacker
With over 500 million records compromised, the 2014 Marriott/Starwood breach was the biggest data breach ever perpetrated by a state-sponsored attacker. In this case, a Chinese intelligence group was reportedly behind the incident.
The cost to Marriott was actually far smaller than many would expect. Overall, the breach cost a mere $72 million during the first six months, the majority of which was actually covered by insurance. [Source: Washington Post & CNN]
Data Breach Cost Statistics
18. Data Breaches Cost Businesses $150 Per Compromised Record
The per-record cost of data breaches seems modest, coming in at $150 per stolen, lost, or compromised record. However, that means 10,000 records would come with a price tag of $1.5 million. If there were 1 million records, that totals to $150 million. [Source: IBM]
19. Breaches Originating from Third-Parties Cost $370,000 More on Average
On average, third-party-related breaches, such as those originating from partners or suppliers or their systems, cost $370,000 more than those originating within the company. This highlights the importance of thorough vetting, particularly when it comes to partner and supplier security standards, practices, and protocols. [Source: IBM]
20. Data Breaches in the United States Cost More Than Double the Worldwide Average
The average cost of a data breach in the United States far outpaces international numbers. At $8.19 million, that makes the average cost of a U.S. incident more than double the worldwide average. [Source: IBM]
21. Companies Involved in Large Data Breaches Underperform by More Than 15% Following the Incident
When it comes to long-term ramifications, a single data breach can harm a company’s financial performance for years. Overall, companies that experienced a breach involving 1+ million records and were publicly listed at the time of the incident underperform the market by 15.6% a full three years after the fact. [Source: Comparitech]
22. At $4 Billion, Epsilon Data Breach Was the Most Costly of All Time
The 2011 Epsilon breach was the most costly data breach of all time, running a total cost of $4 billion. In the breach, email data from 75 client companies was compromised, including on major companies such as Best Buy and Target. Though the information was only stolen on 2% of customers, the size of the email lists and clients involved meant millions of contact details were involved in the breach. [Source: CSO Online]
More Data Breach Statistics
23. Data Breaches Double Across Manufacturing and Utilities in 2021
While data breach activity increases in the vast majority of sectors, the manufacturing and utilities industries were definitively the hardest hit. They represent the biggest overall increase, with the number of breaches more than doubling between 2020 and 2021. [Source: CNET]
24. The U.S. Military Experienced Zero Reported Data Breaches in 2021
When it comes to anomalous data breach activity, the military actually saw a decline in breaches. In fact, the U.S. military didn’t report a single data breach in 2021. [Source: CNET]
25. California Experienced the Most Data Breaches, with 5.6 Billion Records Compromised Over 15 Years
Between 2005 and mid-2020, California had the most data breaches. In total, there were 1,777 reported incidents involving 5.6 billion records. That’s over twice the number of breaches of second-place New York, which had 863 reported breaches. [Source: Comparitech]
26. Ukraine Targeted by 67% Fewer Data Breaches in Q1 2022
Prior to the invasion, during Q4 2021, Ukraine was the most breached country in Eastern Europe. While data breaches are rising in Russia, Ukraine saw a dramatic decline.
Overall, the nation was involved in 67% fewer breaches during the quarter prior to the invasion. Likely, this is a result of compromised communication services, though public sentiment regarding the war may also be a factor. [Source: Surfshark]
July 8, 2022 Feature: Heyday or Doomsday? Banks and Regulators at Odds Over CBDCs
Courtesy of PYMNTS.com
 The Federal Reserve asked the public for its thoughts on the need for a central bank digital currency (CBDC), and the banking industry has answered with a resounding “no.”
The Federal Reserve asked the public for its thoughts on the need for a central bank digital currency (CBDC), and the banking industry has answered with a resounding “no.”
The comments came in response to the Fed’s report, “Money and Payments: The U.S. Dollar in the Age of Digital Transformation.”
While the Fed itself has been opposed and undecided, the idea has caught hold around the world, with China on the verge of taking its digital yuan live, India promising a digital rupee, and the European Union and European Central Bank (ECB) aggressively supporting a digital euro.
Here’s a look at the pros promoted by many central bankers and the cons spelled out by the banking business.
Related Links:
- Senate Crypto Bill Debuts, and Crypto Industry Gets Big Wins
- Crypto Industry Lobby Punching Above Its Weight Class
- As Crypto Spirals, Experts Make the Case for Slower, Safer Regulation
- Still No Plan for US Central Bank Digital Currency After Latest Fed Meeting
- Bank of England to Announce Crypto Regulation
The Power of CBDCs
There are several arguments made by central banks and governments in favor of CBDCs, but the issue largely arose — at least on a global basis — in the wake of the fear of stablecoins competing with fiat currencies after Meta’s abortive 2019 effort to launch an unpegged stablecoin called Libra, which was later renamed Diem.
Here are some of the top arguments central bankers and elected officials make in favor of CBDCs:
- Control is paramount:The stablecoin as a currency competitor has many CBDC proponents up in arms. Central bankers and governments say if citizens turn to privately issued stablecoins over fiat, they will lose the ability to oversee their own economies. That’s largely behind China’s move to create the digital yuan — and India’s push for a digital rupee.
- They hold stablecoins at bay:This has a great deal of crossover with control, but it’s worth noting that China and India have banned stablecoins — and any other cryptocurrencies — for payments. And China has banned crypto outright while India came close and is cracking down on crypto trading.
- They insulate economies:One reason that control is needed, many central bankers say, is that if people turn away from the national currency, the governments will lose vital tools to fight off inflation and economic downturns.
- They facilitate real-time payments:A CBDC would almost by definition require that transactions are available around the clock and every day of the year, and it would also allow for real-time transactions.
- They fight dollarization:The U.S. dollar’s position as the world’s reserve currency, and the economic power that provides, is another target of CDBC supporters. Digital currencies could be used to bypass the dollar’s role in international trade, they say.
- They improve inclusion:Getting the unbanked into the financial system is a major goal in many of the countries looking into CBDCs, particularly in developing nations with large gray economies. That means consumers would be able to transact electronically and likely build up credit.
- They cut cross-border costs:Another big focus of CBDC supporters is the staggeringly high cost of cross-border transactions, which not only have enormous fees — particularly remittances, which run 5% to 7% — but take days to finalize.
Banks See Doomsday
In their responses, the banking lobbies argued that CBDCs like a digital dollar “could present serious risks to financial stability and may provide few, if any, benefits,” in Bank Policy Institute’s (BPI’s) words.
Arguing that a CBDC would “undermine the commercial banking system in the United States and severely constrict the availability of credit to the economy,” the group added that many of the potential benefits of a CBDC are available from other tools ranging from existing real-time payments networks to well regulated — and bank issued — stablecoins.
The American Banking Association (ABA) said if a CBDC’s “objective is to realize the benefit of technological innovation, we should look to leverage novel developments in private money (like real-time payments systems and well-regulated stablecoins).”
Here are the main reasons banks see CBDCs as a threat:
- They create unfair competition:A CBDC would fundamentally change “the relationship between citizens and the Federal Reserve,” the ABA argued, noting that a digital dollar would be a direct liability on the central bank. That would, in effect, move money away from depositary banks and into accounts at the Federal Reserve, where the funds can’t be put to work.
- There would be less to lend:Aside from having to compete with the central bank, commercial institutions would have to hold CBDC deposits in the same way they do securities, BPI said. That means banks “could not do anything with the customer’s CBDC,” deposits, it added. “Any transfer of a dollar deposit from a commercial bank or credit union to a CBDC is a dollar unavailable for lending to businesses or consumers.”
- There are other options:While CDBC proponents have argued that a digital dollar would make both internal and cross-border payments faster, “this rationale for a CBDC seems increasingly inapt in the United States, where The Clearing House’s RTP real-time payment system, operational since 2017, continues to grow in use,” BPI said. The need for 24/7/365 payments is also a feature of the Federal Reserve’s forthcoming FedNow. On the cross-border side, there are other options, such as The Clearing House, EBA CLEARING and SWIFT’s plan to launch an “immediate cross-border (IXB) payments system” by the end of the year, BPI said.
- They defend the dollar:On that point, the BPI turned to CBDC skeptical Federal Reserve Chairman Jerome Powell, who said, “the reason the dollar is the reserve currency is ‘because of our rule of law; our democratic institutions, which are the best in the world; our economy; our industrious people; all the things that make the United States the United States.’”
- The stablecoin threat is overblown:As for the argument that a CBDC is needed to defend against competition from privately-issued stablecoins that could compete with national currencies, BPI called for requiring stablecoins be backed by dollars deposited in commercial banks and treasuries — something the administration recently called for. Unlike CBDCs, BPI said, carefully regulated stablecoins “could avoid undermining the banking system while still offering convenience to customers.”
- Inclusion is already widespread:One of the biggest arguments made around the world for CBDCs is to improve financial inclusion of the unbanked. As for the U.S., both banking groups said that’s just not as big an issue as it is in developing nations. The ABA and BPI pointed to the Bank On program as an example of a better option with minimal opening requirements and costs — and no penalties.
July 1, 2022 Feature: Consumer Trends Report: Peer-to-Peer Payment Services
Courtesy of Maggie Davis, LendingTree
 Convenience is key in today’s fast-paced, technology-oriented world. With peer-to-peer (P2P) service apps like PayPal and Venmo offering simple ways to make digital transactions, it’s not much of a surprise that they’ve grown in popularity. Today, more than 8 in 10 (84%) consumers say they’ve used a P2P service.
Convenience is key in today’s fast-paced, technology-oriented world. With peer-to-peer (P2P) service apps like PayPal and Venmo offering simple ways to make digital transactions, it’s not much of a surprise that they’ve grown in popularity. Today, more than 8 in 10 (84%) consumers say they’ve used a P2P service.
But P2P apps don’t come without risks. Some users are losing money through mistakes and scams — and the most frequent users are at an increased risk, according to the latest LendingTree survey of nearly 1,200 U.S. consumers. Keep reading for more on what consumers know about P2P service liability, and how users can better protect their transactions.
TABLE OF CONTENTS
- Key findings
- Majority of consumers have used P2P service apps
- Common fraud and security concerns put users at risk
- 69% know users are liable for losing money, but only 44% believe they should be
- Users who keep a balance wrongly believe they’re covered by FDIC insurance
- Consumers think other payment methods are more secure
- Methodology
Key Findings
- Consumers are increasingly turning to peer-to-peer payment (P2P) service apps. 84% of consumers have used P2P services; among users, 44% utilize P2P services at least once a week. PayPal — the spearheader of P2P payments — is the most popular service among consumers (84%), followed by Venmo (49%).
- Amid a jump in popularity, security and fraud concerns put P2P users at risk of losing money. Nearly a quarter (23%) of P2P users have sent money to the wrong person, and 15% have been victims of scams. For those who use P2P services several times a week, those percentages jump to 42% and 22%, respectively.
- Most consumers know users are liable for P2P fraud, even if they disagree. 69% of Americans correctly identify users as liable for losing money in a scam, but only 44% believe they should.
- Though P2P services are growing, they’re not FDIC insured. 62% of consumers knew FDIC doesn’t insure P2P balances. However, 49% of those who keep a balance wrongly believe their money is protected.
- Consumers think other payment methods are more secure. 31% of consumers believe bank transfers are the most secure payment method — ranking highest overall. Comparatively, just over 1 in 10 (11%) believe P2P services are the most secure. Among the 16% of consumers who say they don’t use P2P service apps, 18% say security is their top concern.
Majority of consumers have used P2P service apps
Overall, 84% of consumers say they’ve used a P2P service app. That figure crosses the 90% threshold among Gen Zers (ages 18 to 25) and millennials (ages 26 to 41), with both at 91%.
PayPal is the most popular service among consumers (84%), followed by Venmo (49%).
However, younger users are more inclined to use newer services. For example, 71% of Gen Zers on a P2P platform say they utilize Venmo, and 61% say so for CashApp.
Those who’ve used P2P services typically make frequent transactions — 44% complete one at least once weekly. And among younger users, that’s particularly true: In fact, 37% of Gen Zers and 36% of millennials use P2P services multiple times a week. While Gen Xers (ages 42 to 56) aren’t far behind (28%), just 7% of baby boomers (ages 57 to 76) report using P2P services as frequently.
Among the most common reasons people utilize P2P services, users are most likely to pay their loved ones (58%) or gift money (43%). Other common P2P transactions include:
- Food and dining (41%)
- Clothing (33%)
- Groceries (28%)
- Entertainment (27%)
- Gas (26%)
- Living expenses, such as rent or utilities (21%)
- Other (13%)
- Charitable donations (10%)
- Rideshare services (10%)
- Travel (10%)
- School or work-related events/activities (8%)
For Gen Z users, however, food and dining (70%) is the No. 1 reason for utilizing P2P services; they’re also most likely to use it for purchasing clothing (50%). And while millennials are pretty in line with the averages for P2P payment uses, they’re most likely to utilize the services to make charitable donations (14%).
While nearly 9 in 10 (86%) users say they only use their accounts for personal reasons, some consumers also utilize P2P apps for business transactions. However, most of them don’t bother making a separate business account — among all consumers on P2P platforms, 11% say they use their accounts for both personal and business transactions. Just 3% say they have separate accounts.
Although making a separate business account may not be required (some apps, like Venmo and PayPal, allow users to tag transactions as business payments), new IRS reporting requirements could spell trouble for some businesses during the next tax season.
The threshold for a 1099-K — the tax form used to report payments received by a business or individual for the sale of goods and services on a third-party network — is significantly lower than in previous years. P2P services are now required to send a 1099-K to those who report $600 or more in business transactions, for any number of transactions, on their apps. Previously, the threshold was $20,000 and more than 200 transactions in a calendar year.
It’s important to note that the reporting requirement doesn’t apply to most personal transactions or other amounts generally excluded from gross income. This includes:
- Amounts from selling personal items at a loss
- Reimbursements
- Money received as gifts from friends and family
If a P2P service provider isn’t able to identify all of a user’s business payments, those who don’t take the time to distinguish their business payments from their personal transactions run the risk of inaccurately reporting incomes on their tax forms.
![]() Click here to read the entire report or use the bullets at the top to navigate to specific topics.
Click here to read the entire report or use the bullets at the top to navigate to specific topics.
June 24, 2022 Feature: Flagstar Bank Data Breach Affects 1.5 Million Customers
Courtesy of By Eduard Kovacs, Security Week
June 21, 2022 — Michigan-based Flagstar Bank, which has more than 150 branches across several US states, has disclosed a data breach that involved threat actors accessing files containing the personal information of 1.5 million individuals.
Related Reading:
- NCUA Chairman Todd M. Harper Remarks at the NASCUS/CUNA Cybersecurity Conference
- Morgan Stanley Hit by Accellion Hack Through Third-Party Vendor
- Accellion Reaches $8.1 Million Settlement Over FTA Data Breach
- P&N Bank Data Breach Exposes Trove of User Data
 According to a data breach notification posted on Flagstar’s website and information provided by the company to authorities, the breach occurred in early December 2021. An investigation finalized on June 2 showed that the attackers had accessed files storing personal information.
According to a data breach notification posted on Flagstar’s website and information provided by the company to authorities, the breach occurred in early December 2021. An investigation finalized on June 2 showed that the attackers had accessed files storing personal information.
It seems that different types of data were compromised for different customers, but the attacker appears to have obtained the social security numbers of at least some people. Affected individuals are being notified through snail mail.
The company said it does not have evidence that the compromised information has been misused, but it has decided to provide affected individuals two years of free identity monitoring services. It’s unclear if the attack involved ransomware or any other type of malware. SecurityWeek has reached out to Flagstar for clarifications and will update this article if the company responds.
This is not the first time Flagstar has been targeted by cybercriminals. In March 2021, the bank started informing customers that it was one of the many companies affected by a hack involving a file transfer service from Accellion.
The Accellion service was compromised in late 2020, allowing cybercriminals to access the files of tens of organizations that had been using the service. In March 2021, the Cl0p ransomware gang published data stolen from Flagstar on its leak website. The Accellion incident also impacted nearly 1.5 million Flagstar customers and the financial institution ended up reaching a $5.9 million deal to end litigation.
 Related Reading: Alarming Cyber Statistics For Mid-Year 2022 That You Need To Know
Related Reading: Alarming Cyber Statistics For Mid-Year 2022 That You Need To Know
Courtesy of Chuck Brooks, Global Thought Leader in Cybersecurity and Emerging Tech, Forbes
A couple of times per year, I take a deep dive on writing about the newly reported cybersecurity statistics and trends that are impacting the digital landscape. Unfortunately, despite global efforts, every subsequent year the numbers get worse and show that we are far from being able to mitigate and contain the numerous cyber-threats targeting both industry and government.
Below is a synopsis with links on some of the recent cyber developments and threats that CISOs need to key a close watch on (and that you need to know) for the remaining part of 2022 and beyond.
While many of the statistics seem dire, there is some positive aspect on the trends side as the cybersecurity community has been taking several initiatives to create both cyber awareness and action. And for those attending the 2022 RSA Conference in San Francisco, hopefully the backdrop of the following statistics and trends from mid-year 2022 can also be useful to analyze and match with product and services roadmaps for cybersecurity.
Link: Cybercriminals can penetrate 93 percent of company networks (betanews.com)
“In 93% of cases, an external attacker can breach an organization’s network perimeter and gain access to local network resources.
This is among the findings of a new study of pen testing projects from Positive Technologies, conducted among financial organizations, fuel and energy organizations, government bodies, industrial businesses, IT companies and other sectors.
An attacker’s path from external networks to target systems begins with breaching the network perimeter. According to the research, on average, it takes two days to penetrate a company’s internal network. Credential compromise is the main route in (71 percent of companies), primarily because of simple passwords being used, including for accounts used for system administration.”
June 17, 2022 Feature: 2022 Cannabis Banking Symposium Recap

Click here to view the 2022 2022 Cannabis Banking Symposium photo gallery.
Hosted in beautiful Aurora, Colorado, the 2022 NASCUS Cannabis Banking Symposium brought together nearly 100 cannabis banking experts, regulators, credit unions, and service providers from across the country to network, learn and collaborate on this pressing issue.
 Guests heard from the country’s most distinguished cannabis banking leaders, including Colorado Governor Jared Polis, who has been a strong industry advocate within the cannabis industry.
Guests heard from the country’s most distinguished cannabis banking leaders, including Colorado Governor Jared Polis, who has been a strong industry advocate within the cannabis industry.
Polis commented, “For over a decade, Colorado has been a leader in the cannabis space, bringing bold and creative businesses to the state.” The week prior to the symposium, Governor Polis signed a bill into law expanding medical marijuana research grant programs.
This event also welcomed special guest and NCUA Board Member, the Honorable Rodney Hood. Board Member Hood’s presentation focused on a core theme, the need to “reform our banking laws to accommodate the change in legal status of cannabis and marijuana businesses in the United States.” Hood has spoken out several times to “spur action” in Congress to reform cannabis banking laws.
 “It is time for federal action to clarify and harmonize the laws and regulations surrounding the state-legal cannabis industry and marijuana-related businesses, so that this industry can take part in the legitimate financial services industry,” stated Hood.
“It is time for federal action to clarify and harmonize the laws and regulations surrounding the state-legal cannabis industry and marijuana-related businesses, so that this industry can take part in the legitimate financial services industry,” stated Hood.
Related Reading: Read NCUA Board Member Rodney E. Hood’s Full Remarks at the NASCUS 2022 Cannabis Banking Symposium Aurora, Colorado
In a world of “cannabis-curious” entities (businesses and individuals), credit unions, state supervisors, and service providers are working together to define rapidly evolving technologies and determine the best approaches and regulation practices.
Additional presentations included panel discussions covering recent developments in state legalization initiatives, the importance of data analytics and compliance, hemp-related regulatory updates, impacts on insurance coverage, and more.
At this time, we would like to offer a special thank you to our Colorado hosts, the Colorado Department of Regulatory Agencies; Division of Financial Services, Executive Director Patty Salazar, and Mark Valente, Commissioner of Financial Services, as well as Mike Williams, President/CEO, Colorado Credit Union.
June 10, 2022 Feature: Lawsuits Over Zelle Pile Up
Courtesy of Lynne Marek, Payments Dive
 June 6, 2022 — Bank of America was sued last month by a customer claiming that the bank failed to reimburse him for fraudulent losses incurred when he used its Zelle money transfer service, echoing the claims against Zelle in an April lawsuit brought against another bank, Wells Fargo. Both lawsuits seek class-action status.
June 6, 2022 — Bank of America was sued last month by a customer claiming that the bank failed to reimburse him for fraudulent losses incurred when he used its Zelle money transfer service, echoing the claims against Zelle in an April lawsuit brought against another bank, Wells Fargo. Both lawsuits seek class-action status.
In the latest case, plaintiff Mohammad Al-Ramahi alleges he was tricked into sending $4,950 through Zelle in April 2020 as part of a scam in which he thought he was sending the money in his role at a new job. When he discovered that wasn’t the case and that his money was gone, Bank of America refused to reimburse him for the loss, he alleges in his lawsuit filed on May 27 in U.S. District Court for the Northern District of California. He alleges further that the bank didn’t warn him about the risk of such losses when using the person-to-person payment app.
![]() Read More: Capital One Class Action Alleges Company Does Not Assist Victims of Zelle Fraud
Read More: Capital One Class Action Alleges Company Does Not Assist Victims of Zelle Fraud
- Who: A customer sued Capital One, claiming the bank didn’t disclose the security risks of using money transfer service Zelle.
- Why: The plaintiff says he and other Capital One customers were scammed through Zelle, yet the bank declined to reimburse them.
- Where: The case was filed in Florida federal court.
“The unique, misrepresented, and undisclosed architecture of the Transfer App payment systems and BofA’s own fraud policies means…that virtually any money transferred for any reason via a Transfer App is gone forever, without recourse, reimbursement, or protection for victimized Accountholders,” the lawsuit says. That runs counter to the bank’s marketing of Zelle as a “fast, safe and secure way” to send money, the plaintiff alleged.
Bank of America and Wells Fargo declined to comment. Zelle didn’t immediately respond to an emailed request for comment.
Legal parameters in the area are in flux, said one lawyer who specializes in payments. “For decades the consumer protection regulations regarding electronic fund transfers said a bank was not liable for a payment if consumers willingly provided their credentials to another party, even if the purchase generating the payment turned out to be fraudulent,” attorney Stephen Middlebrook said in commenting on the litigation. The Consumer Financial Protection Bureau “is trying to change the rule so that now the bank is liable for so-called ‘unauthorized transactions’ even when the consumer freely consented to the transaction.”
The Zelle business, launched in 2017, is a subsidiary of Scottsdale, Arizona parent company Early Warning Services, which in turn is owned by the biggest U.S. banks, including Bank of America and Wells Fargo. The lawsuit says that users sent $490 billion over the app last year.
Read More: Raising Zelle: Furious P2P Users Take Banks to Court
It also alleges that some 18 million Americans were defrauded in similar schemes perpetrated on person-to-person money transfer apps like Zelle in 2020, according to industry consulting firm Javelin Strategy and Research. The New York Times chronicled extensive fraud allegations related to Zelle in a March feature in which the banks deflected responsibility mainly by saying the consumers authorized the payments.
The plaintiff argues that the bank’s failure to protect consumers is a breach of contract for fair dealing and violates California laws designed to protect consumers. “BofA maintains a secret policy whereby it refuses to reimburse fraud losses incurred via Zelle, even where its accountholders timely inform BofA of the fraud,” the lawsuit said. “BofA misrepresents and fails to disclose this secret policy.”
The lawsuit cites a letter by U.S. Senate Democrats Elizabeth Warren and Robert Menendez that questioned Zelle parent Early Warning Services over “disturbing reports of a rise in fraud.” In the May letter, the lawmakers sought information on the dollar value of the overall reported fraud, the number of cases in which Zelle provided refunds — and the value of those refunds — and the number of cases Zelle referred to law enforcement or banking regulators.
In the earlier April lawsuit against Wells Fargo, filed in U.S. District Court for the Central District of California, the plaintiff Jessica Stock alleged she lost $1,000 as a result of a scam at that bank that involved Zelle. In the fraud, she received a call in December 2021 from a person who purported to be a Wells Fargo employee, but was not, and who persuaded her to share a verification code that allowed the fraudster to take the money from her checking account, the lawsuit said.
June 3, 2022 Feature: New Research Indicates There’s Much More to be Done to Fight Fraud
Frontline fraud fighters believe there’s much more to be done in the multi-billion-dollar battle against fraud, according to research released in May 2022.
 New research from ID Insight, a national leader in developing platform-based fraud-prevention solutions for business, and About-Fraud, a global community for fraud fighters, surveyed fraud investigators, managers and directors on their roles within financial services companies.
New research from ID Insight, a national leader in developing platform-based fraud-prevention solutions for business, and About-Fraud, a global community for fraud fighters, surveyed fraud investigators, managers and directors on their roles within financial services companies.
While there’s consensus that financial services companies today are doing a better job than ever before of preventing fraud, the challenge to prevent fraud still exists, and at serious scale — being driven by large, organized crime rings. Respondents feel the technology that allows fraudsters to commit fraud is better than the technology to prevent it, and present recommendations for how their financial service companies can invest to bolster their fraud-fighting capabilities.
Survey Highlights
This first-of-its-kind national survey is the only one to have ever sought the opinions of frontline fraud fighters, providing an important roadmap for organizations to improve their outcomes.
- Fraud fighters recognize that financial services companies are in an arms race against criminals – and savvy fraudsters are well equipped to successfully carry out their schemes. The majority of fraud fighters agree with these statements:
- It’s easier than ever to commit fraud today (82%)
- Customers make it easier for fraudsters to commit fraud (86%)
- There is better technology to commit fraud than there is to prevent it (65%)
- Fraud trends and schemes are changing too quickly to keep up (52%)
- Fraud is committed by large, organized rings (72%)
- Fraudsters are bad criminals who are trying to commit big crimes (68%)
- I need more training to stay current (66%)
- My company’s customer experience initiatives make it easier for fraudsters to commit fraud (57%)
- Eight out of 10 (81 percent) of respondents say financial services companies could be doing more to fight fraud. At the same time, fraud fighters are complimentary of their employers’ efforts. The majority of fraud fighters agree with these statements:
- My company does a good job of preventing fraud (90%)
- Financial institutions are doing a better job today at preventing fraud (83%)
- I am compensated fairly for my work (70%)
- Fighting fraud is a top priority for my employer/organization (67%)
 More than a third of fraud fighters (34 percent) cite new tools or services as the single-most-important investment an organization could make to manage fraud more effectively.In response to the single most important investment fraud fighters thought their organization could make to manage fraud more effectively, respondents indicated:
More than a third of fraud fighters (34 percent) cite new tools or services as the single-most-important investment an organization could make to manage fraud more effectively.In response to the single most important investment fraud fighters thought their organization could make to manage fraud more effectively, respondents indicated:
- 34% New tools or services to combat fraud
- 18% Availability of real-time data
- 13% More people added to the fraud team
- 12% More people to identify, detect, prevent, and mitigate fraud
- 12% Availability of enterprise-wide data
- 6% Better/more training
- 3% Better way to prioritize fraud investigations and alerts
- Fraud fighters are motivated by doing good. The majority of fraud fighters agree with these statements:
- I am performing an important role for my organization (98%)
- I can prevent fraud from happening in the future (97%)
- I am doing something good for our customers (96%)
- I am making a difference in the world (95%)
- I can stop fraud (92%)
- My work is valued by my organization (91%)
- Most fraud fighters are passionate about their vocation. 81% of respondents collaborate or share insights and ideas with fraud fighters working at other institutions at least a few times a year, with 33% of those collaborating weekly or dailyThe majority of fraud fighters agree with these statements:
- I am willing to spend time outside of business hours learning about emerging fraud trends (95%)
- I intend to dedicate my career to fighting fraud (92%)
- I want to earn an industry certification during the next 12 months (69%)
Who Participated in This Survey?
100+ respondents completed the survey, the vast majority of whom spend “100% of their time” or are “mostly” dedicated to fraud fighting activities in their bank, credit union, payments company, lender, or other type of financial services company.
- One quarter (25%) of the respondents have worked in a role that identifies, detects, prevents, or mitigates fraud for less than five years, while 48% have been in the field for 10 years or more.
- 80% have earned at least a four-year college degree, with 26% of those holding a graduate degree.
- 50% worked in another role within a financial services company before becoming a fraud fighter.
- 23% were working in an unrelated industry before becoming a fraud fighter.
- 62% said there are seven or fewer fraud fighters on their functional team.
Research Methodology: An online quantitative survey was conducted with professionals who are in a fraud fighter role within the financial services industry. Data collection took place from September 21, 2021 – December 5, 2021. Around 100 respondents completed all the survey questions. ID Insight and About-Fraud worked together to identify potential participants for this research from their organizational databases, contacts in the industry, and referrals from colleagues.
May 27, 2022 Feature: The Case for Placing AI at the Heart of Digitally Robust Financial Regulation
Courtesy of Jo Ann Barefoot, Brookings Center on Regulation and Markets Policy Brief
May 24, 2022 —“Data is the new oil.” Originally coined in 2006 by the British mathematician Clive Humby, this phrase is arguably more apt today than it was then, as smartphones rival automobiles for relevance, and the technology giants know more about us than we would like to admit.
![]()
Click here to download the policy briefing.
Just as it does for the financial services industry, the hyper-digitization of the economy presents both opportunity and potential peril for financial regulators. On the upside, reams of information are newly within their reach, filled with signals about financial system risks that regulators spend their days trying to understand. The explosion of data sheds light on global money movement, economic trends, customer onboarding decisions, quality of loan underwriting, noncompliance with regulations, financial institutions’ efforts to reach the underserved, and much more. Importantly, it also contains the answers to regulators’ questions about the risks of new technology itself. Digitization of finance generates novel kinds of hazards and accelerates their development. Problems can flare up between scheduled regulatory examinations and can accumulate imperceptibly beneath the surface of information reflected in traditional reports. Thanks to digitization, regulators today have a chance to gather and analyze much more data and to see much of it in something close to real time.
The potential for peril arises from the concern that the regulators’ current technology framework lacks the capacity to synthesize the data. The irony is that this flood of information is too much for them to handle. Without digital improvements, the data fuel that financial regulators need to supervise the system will merely make them overheat.
 Enter artificial intelligence.
Enter artificial intelligence.
In 2019, then-Bank of England Gov. Mark Carney argued that financial regulators will have to adopt AI techniques in order to keep up with the rising volumes of data flowing into their systems. To dramatize the point, he said the bank receives 65 billion pieces of data annually from companies it oversees and that reviewing it all would be like “each supervisor reading the complete works of Shakespeare twice a week, every week of the year.”
That was three years ago. The number is almost certainly higher today. Furthermore, the numbers he cited only covered information reported by regulated firms. It omitted the massive volumes of external “Big Data” generated from other sources like public records, news media, and social media that regulators should also be mining for insight about risks and other trends.
AI was developed over 70 years ago. For decades, enthusiasts predicted that it would change our lives profoundly, but it took awhile before AI had much impact on everyday lives.1 AI occasionally made news by performing clever feats, like IBM’s Watson besting human champions at Jeopardy in 2011, or AIs beating masters of complex games like chess (in 1996) and Go (in 2017). However, it was only recently that such machines showed signs of being able to solve real-world problems. Why is that?
A key answer is that, until only recently, there wasn’t enough data in digitized form—formatted as computer-readable code—to justify using AI.2 Today, there is so much data that not only can we use AI, but in many fields like financial regulation we have to use AI simply to keep up.
As discussed further below, financial regulators around the world are in the early stages of exploring how AI and its sub-branches of Machine Learning (ML), Natural Language Processing (NLP), and neural networks, can enhance their work. They are increasingly weighing the adoption of “supervisory technology” (or “suptech”) to monitor companies more efficiently than they can with analog tools. This shift is being mirrored in the financial industry by a move to improve compliance systems with similar “regulatory technology” (“regtech”) techniques. Both processes are running on a dual track, with one goal being to convert data into a digitized form and the other to analyze it algorithmically. Meeting either of these objectives without the other has little value. Together, they will transform both financial regulation and compliance. They offer the promise that regulation, like everything else that gets digitized, can become better, cheaper, and faster, all at once.
Imagine if AI was already the default mechanism
Financial regulators around the world have generally been more active in regulating industry’s use of AI than adopting it for their own benefit. Opportunities abound, however, for AI-powered regulatory and law enforcement tactics to combat real-world problems in the financial system. In a later section, this paper will look at the primary emerging use cases. Before doing so, it is worth taking a look at some areas of poor regulatory performance, both past and present, and ask whether AI could have done better.
One example is the $800 billion Paycheck Protection Program that Congress established in 2020 to provide government-backed loans for small businesses reeling from the pandemic. More than 15% of PPP “loans” —representing $76 billion—contained evidence of fraud, according to a study released last year. Many cases involved loan applicants using fake identities. Imagine if the lenders submitting loan guarantee applications or the Small Business Administration systems that were reviewing them had had mature AI-based systems that could have flagged suspicious behavior. They could have spotted false statements and prevented fraudulent loans, thereby protecting taxpayer money and ensuring that their precious funds helped small businesses in need instead of financing thieves.
Two examples can be found from the war in Ukraine. The Russian invasion has sparked a whole new array of sanctions against Russian oligarchs who hide riches in shell companies and are scrambling to move their money undetected. Financial institutions are required to screen accounts and transactions to identify transactions by sanctioned entities. What if they and law enforcement agencies like the Financial Crimes Enforcement Network (FinCEN) had AI-powered analytics to pull and pool data from across the spectrum of global transactions and find the patterns revealing activity by sanctioned parties? Unfortunately, most financial institutions and government agencies do not have these tools in hand today.
The second example comes from the rapid flight of millions of refugees attracting human traffickers to the country’s borders seeking to ensnare desperate women and children and sell them into slavery for work and sex. Banks are required by law to maintain anti-money laundering (AML) systems to detect and report money movement that may indicate human trafficking and other crimes, but these systems are mostly analog and notoriously ineffective. The United Nations’ Office on Drugs and Crime estimates that less than 1% of financial crime is caught. AI-powered compliance systems would have a far better chance of flagging the criminal rings targeting Ukraine. If such systems had been in effect in recent years, moreover, the human trafficking trade might not be flourishing. As it stands today, an estimated 40 million people are being held captive in modern human slavery, and one in four of them is a child.
In another thought experiment, what if bank regulators in 2007 had been able to see the full extent of interrelationships between subprime mortgage lenders and Wall Street firms like Bear Stearns, Lehman Brothers, and AIG? If regulators had been armed with real-time digital data and AI analytics, they would have been monitoring risk contagion in real time. They might have been able to avert the financial crisis and with it, the Great Recession.
Finally, what about fair lending? In 1968, the United States outlawed discrimination on the basis of race, religion and other factors in mortgage lending through the passage of the Fair Housing Act.3 With the later passage of the Equal Credit Opportunity Act and Housing and Community Development Act, both in 1974, Congress added sex discrimination to that list and expanded fair-lending enforcement to all types of credit, not just mortgages.4That was nearly 50 years ago.
These laws have gone a long way toward combating straightforward, overt discrimination but have been much less effective in rooting out other forms of bias. Lending decisions still produce “disparate impacts” on different groups of borrowers, usually in ways that disproportionately harm protected classes like people of color. Some of this arises from the fact that high volume credit decisioning must rely on efficient measures of creditworthiness, like credit scores, that in turn rely on narrow sources of data.5 What if, 40 years ago, both regulators and industry had been able to gather much more risk data and analyze it with AI? How many more people would have been deemed creditworthy instead of having their loan denied? Over four decades, could AI tools have changed the trajectory of racial opportunity in the United States, which currently includes a $10 trillion racial wealth gap and the African-American homeownership rate lagging that of whites by 30 percentage points?
 How regulators aim to keep pace with exponentially changing tech
How regulators aim to keep pace with exponentially changing tech
In his 2018 book titled “Unscaled,” venture capitalist Hemant Taneja argued that exploding amounts of data and AI will continue to produce unprecedented acceleration of our digital reality. “In another ten years anything that AI doesn’t power will seem lifeless and outmoded. It will be like an icebox after electric-powered refrigerators were invented,” he wrote.
Taneja’s estimated time horizon is now only six years away. In the financial sector, this sets up a daunting challenge for regulators to design and construct sufficiently powerful suptech before the industry’s changing technology could overwhelm their supervisory capacity. Fortunately, regulators in the U.S. and around the world are taking steps to narrow the gap.
Arguably the global leader in regulatory innovation is the United Kingdom’s Financial Conduct Authority (FCA). In 2015, the FCA established the Project Innovate initiative, which included the creation of a “regulatory sandbox” for private sector firms to test new products for their regulatory impact. A year later, the FCA launched a regtech unit that developed what the agency called “techsprints”—an open competition resembling a tech hackathon in which regulatory, industry, and issue experts work side-by-side with software engineers and designers to develop and present tech prototypes for solving a particular regulatory problem. The innovation program has since been expanded into a major division within the FCA.6
The FCA has been able to translate this relatively early focus on digital innovation into real-world problem solving. In 2020, a senior agency official gave a speech about how the FCA uses machine learning and natural language processing to monitor company behaviors and “spot outlier firms” as part of a “holistic” approach to data analysis. Similar strides have been made in other countries, including Singapore and Australia.
U.S. regulators for the most part have made slower progress incorporating AI technologies in their monitoring of financial firms. All of the federal financial regulatory bodies have innovation programs in some form. Most of them, however, have focused more on industry innovation than their own. The U.S. banking agencies—Consumer Financial Protection Bureau, Federal Deposit Insurance Corporation, Federal Reserve Board and Office of the Comptroller of the Currency—all have innovation initiatives that are largely outward-facing, aimed at understanding new bank technologies and offering a point of contact on novel regulatory questions. They all also expanded their technology activities during the COVID-19 pandemic, spurred by the sudden digital shifts underway in the industry and their own need to expand offsite monitoring. Several agencies also have suptech projects underway. These, however, generally have limited reach and do not address the need for agencies to revisit their foundational, analog-era information architecture.
This is beginning to change. The Federal Reserve in 2021 created the new position of Chief Innovation Officer and hired Sunayna Tuteja from the private sector, charging her to undertake a sweeping modernization of the Fed’s data infrastructure. The FDIC, too, has closely examined its own data structures, and the OCC has worked on consolidating its examination platforms. These are productive steps, but they still lag the advanced thinking underway in other parts of the world. U.S. regulators have yet to narrow the gap between the accelerating innovation in the private sector and their own monitoring systems.
Other U.S. regulatory agencies have embraced AI technologies more quickly. In 2017, Scott Bauguess, the former deputy chief economist at the Securities and Exchange Commission (SEC), described his agency’s use of AI to monitor securities markets. Soon after the financial crisis, he said, the SEC began “simple text analytic methods” to determine if the agency could have predicted risks stemming from credit default swaps before the crisis. SEC staff also applies machine-learning algorithms to identify reporting outliers in regulatory filings.
Similarly, the Financial Industry Regulatory Authority (FINRA)—the self-regulatory body overseeing broker-dealers in the U.S.—uses robust AI to detect possible misconduct.7 The Commodity Futures Trading Commission (CFTC), meanwhile, has been a leader through its LabCFTC program, which addresses both fintech and regtech solutions. Former CFTC Chairman Christopher Giancarlo has said that the top priority of every regulatory body should be to “digitize the rulebook.”8 Lastly, the Treasury Department’s Financial Crimes Enforcement Network (FinCEN) launched an innovation program in 2019 to explore regtech methods for improving money-laundering detection.9 The agency is now in the process of implementing sweeping technology mandates it received under the Anti-Money Laundering Act of 2020, a great opportunity to implement AI to better detect some of the financial crimes discussed above.
 Key financial regulation use cases
Key financial regulation use cases
If government agencies supplanted their analog systems with a digitally native design, it would optimize the analysis of data that is now being under-utilized. The needles could be found in the haystack, fraudsters and money launderers would have a harder time hiding their activity, and regulators would more completely fulfill their mission of maintaining a safer and fairer financial system.
Below are specific use cases for incorporating AI in the regulatory process:
AML and sanctions screening
Arguably the most advanced regtech use case globally is anti-money laundering (AML). AML compliance costs the industry upwards of $50 billion per year in the U.S., as most banks rely on rules-based transaction monitoring systems.10 These methods help them determine which activity to report to FinCEN as suspicious but currently produce a false-positive rate of over 90%. This suggests banks, regulators, and law enforcement authorities are spending time and money chasing down potential leads but not really curbing illicit financial crimes. The AML data that law enforcement agencies currently receive contains too much unimportant information and is not stored in formats to help identify patterns of crime.11
Financial regulators around the world have generally been more active in regulating industry’s use of AI than adopting it for their own benefit.
In addition to the challenges associated with locating financial crimes among the massively complex web of global transactions, banks also must perform identity verification checks on new customers and submit “beneficial owner” data to FinCEN to prevent launderers from hiding behind fake shell companies. The war in Ukraine and toughening of sanctions on Russian oligarchs has highlighted the need for better screening mechanisms to restrict the financial activity of individuals that appear on sanctions lists. While a growing industry of regtech firms are attempting to help financial institutions more efficiently comply with Know-Your-Customer (KYC) rules, FinCEN is in the midst of implementing legislative reforms requiring corporations to submit data to a new beneficial owner database.
In 2018 and 2019, the FCA held two international tech sprints aimed at addressing AML challenges. The first sprint dealt with enabling regulators and law enforcement to share threat information more safely and effectively. The second focused on “Privacy-Enhancing Technologies,” or PET’s, of various kinds. For example, homomorphic encryption is a technique that shows promise for enabling data shared through AML processes to be encrypted throughout the analytical process, so that the underlying information is concealed from other parties and privacy is preserved. Another PET technique known as zero-knowledge proof enables one party to ask another essentially a yes-or-no question without the need to share the underlying details that spurred the inquiry. For example, one bank could ask another if a certain person is a customer, or if that person engaged in a certain transaction. Techniques like this can be used to enable machine-learning analysis of laundering patterns without compromising privacy or potentially undermining the secrecy of an ongoing investigation.
Fraud prevention
The SBA did make efforts to evaluate AI tools to detect fraud in PPP loans, looking to certain AI-powered fintech lenders. Nevertheless, the small business loan program was still rife with fraud. (In fact, some of the attention regarding fraud concerns has centered on loans processed by fintech firms.12) Several studies show that effective use of machine learning in credit decisioning can more easily detect when, for example, loan applications are submitted by fake entities.
One of the biggest fraud threats facing financial institutions is the use of synthetic identities by bad actors. These are created by combining real customer information with fake data in a series of steps that can fool normal detection systems but can often be caught by regtech analysis using more data and machine learning.
Many regtech solutions for fighting money laundering grew out of technology for identifying fraud, which has generally been more advanced. This may be because the industry has an enormous financial interest in preventing fraud losses. It may also reflect the fact that, in fraud, firms are usually dealing with the certainty of a problem, whereas in AML, they usually never know whether the “Suspicious Activity Reports” they file with FinCEN lead to something useful. These factors make it all the more important to equip banks and their regulators with tools that can more easily, and less expensively, detect patterns of crime.
Consumer protection and financial inclusion
U.S. consumer protection law bans Unfair and Deceptive Acts and Practices (UDAP), both in the financial sector and overall, and adds the criterion of “abusive” activity for purposes of enforcement by the Consumer Financial Protection Bureau (UDAAP). However, enforcement of subjective standards like “unfairness” and “deception” is challenging, often hampered by the difficulty of detecting and analyzing patterns of potentially illegal behavior. As with discrimination, UDAAP enforcement relies on considerable subjective judgment in distinguishing activities that are against the law from more benign patterns. This also makes compliance difficult. AI-based regtech can bring to bear the power of more data and AI analytical tools to solve these challenges, allowing regulators to detect and prove violations more easily. It might also enable them to issue more clear and concrete guidance—including more sophisticated standards on statistical modeling—to help industry avoid discrimination and being responsible for UDAAPs.
There is a growing recognition among advocates that full financial inclusion, especially for emerging markets, requires greatly expanded use of digital technology. Access to cell phones has, in effect, put a bank branch in the hands of two-thirds of the world’s adults. This unprecedented progress has, in turn, highlighted barriers to further success, most of which could be solved or ameliorated with better data and AI.
One is the problem of AML “de-risking.” As noted above, banks must follow Know-Your-Customer (KYC) rules before accepting new customers, a process that includes verifying the person’s identity. In many developing countries, poor people—and particularly women—lack formal identity papers like birth certificates and driver’s licenses, effectively excluding them from access to the formal financial system.13 In some parts of the world, the regulatory pressure on banks to manage risk associated with taking on new customers has resulted in whole sectors—and, in some countries, the entire population—being cut off from banking services.14 In reality, these markets include millions of consumers who would be well-suited to opening an account and do not present much risk at all. Banks and regulators struggle with how to distinguish high-risk individuals from those who are low risk. A great deal of work is underway in various countries to solve this problem more fully with AI, through the use of “digital identity” mechanisms that can authenticate a person’s identity via their “digital footprints.”
A related challenge is that expanded financial inclusion has produced increased need for better consumer protection. This is especially important for people who are brought into the financial system by “inclusion” strategies and who may lack prior financial background and literacy, making them vulnerable to predatory practices, cyber scams, and other risks. Regulators are using AI chatbots equipped with NLP to intake and analyze consumer complaints at scale and to crawl the web for signs of fraudulent activity.
One example is the RegTech for Regulators Accelerator (R2A) launched in 2016 with backing from the Bill & Melinda Gates Foundation, the Omidyar Network, and USAID.15 It focuses on designing regulatory infrastructure in two countries, the Philippines and Mexico. Emphasizing the need for consumers to access services through their cell phone, the project introduced AML reporting procedures and chatbots through which consumers could report complaints about digital financial products directly to regulators.
Importantly, regtech innovation in the developing world often exceeds that in the major advanced economies. One reason is that many emerging countries never built the complex regulatory infrastructure that is commonplace today in regions like the U.S., Canada, and Europe. This creates an opportunity to start with a clean slate, using today’s best technology rather than layering new requirements on top of yesterday’s systems.
Credit discrimination and predatory lending
Perhaps AI’s greatest financial inclusion promise lies in the emergence of data-centered credit underwriting techniques that evaluate loan applications. Traditional credit underwriting has relied heavily on a narrow set of data—especially the individual’s income and credit history, as reported to the major Credit Reporting Agencies—because this information is easily available to lenders. Credit scores are accurate in predicting default risk among people with good FICO scores (and low risks of default). However, those traditional underwriting techniques skew toward excluding some people who could repay a loan but have a thin credit file (and hence a lower or no credit score) or a complicated financial situation that is harder to underwrite.
AI underwriting is beginning to be used by lenders, especially fintechs. AI is also increasingly being used by financial firms as a regtech tool to check that the main underwriting process complies with fair-lending requirements. A third process, much less developed, is the potential for the same technologies to be used by regulators to check for discrimination by lenders, including structural bias and unintentional exclusion of people who could actually repay a loan. Structural biases often lead to “disparate impact” outcomes. In these cases, regulators assert that a lending policy was discriminatory on the basis of race, gender, or other prohibited factors, not because of intent but because a specific class of consumers endured negative outcomes. Because disparate impact is a legal standard16 and violations of these laws create liability for lenders, these claims may also be made by plaintiffs representing people who argue they have been wronged.
Research conducted by FinRegLab and others is exploring the potential for AI-based underwriting to make credit decisions more inclusive with little or no loss of credit quality, and possibly even with gains in loan performance. At the same time, there is clearly risk that new technologies could exacerbate bias and unfair practices if not properly designed, which will be discussed below.
Climate change
In March 2022, the Securities and Exchange Commission proposed rules for requiring public companies to disclose risks relating to climate change.17 The effectiveness of such a mandate will inevitably be limited by the fact that climate impacts are notoriously difficult to track and measure. The only feasible way to solve this will be by gathering more information and analyzing it with AI techniques that can combine vast sets of data about carbon emissions and metrics, interrelationships between business entities, and much more.
 Challenges
Challenges
The potential benefits of AI are enormous, but so are the risks. If regulators mis-design their own AI tools, and/or if they allow industry to do so, these technologies will make the world worse rather than better. Some of the key challenges are:
Explainability: Regulators exist to fulfill mandates that they oversee risk and compliance in the financial sector. They cannot, will not, and should not hand their role over to machines without having certainty that the technology tools are doing it right. They will need methods either for making AIs’ decisions understandable to humans or for having complete confidence in the design of tech-based systems. These systems will need to be fully auditable.
Bias: There are very good reasons to fear that machines will increase rather than decrease bias. Technology is amoral. AI “learns” without the constraints of ethical or legal considerations, unless such constraints are programmed into it with great sophistication. In 2016, Microsoft introduced an AI-driven chatbot called Tay on social media. The company withdrew the initiative in less than 24 hours because interacting with Twitter users had turned the bot into a “racist jerk.” People sometimes point to the analogy of a self-driving vehicle. If its AI is designed to minimize the time elapsed to travel from point A to point B, the car or truck will go to its destination as fast as possible. However, it could also run traffic lights, travel the wrong way on one-way streets, and hit vehicles or mow down pedestrians without compunction. Therefore, it must be programmed to achieve its goal within the rules of the road.
In credit, there is a high likelihood that poorly designed AIs, with their massive search and learning power, could seize upon proxies for factors such as race and gender, even when those criteria are explicitly banned from consideration. There is also great concern that AIs will teach themselves to penalize applicants for factors that policymakers do not want considered. Some examples point to AIs calculating a loan applicant’s “financial resilience” using factors that exist because the applicant was subjected to bias in other aspects of her or his life. Such treatment can compound rather than reduce bias on the basis of race, gender, and other protected factors. Policymakers will need to decide what kinds of data or analytics are off-limits.
One solution to the bias problem may be use of “adversarial AIs.” With this concept, the firm or regulator would use one AI optimized for an underlying goal or function—such as combatting credit risk, fraud, or money laundering—and would use another separate AI optimized to detect bias in the decisions in the first one. Humans could resolve the conflicts and might, over time, gain the knowledge and confidence to develop a tie-breaking AI.
Data quality: As noted earlier, AI and data management are inextricably intertwined, so that acceptable AI usage will not emerge unless regulators and others solve the many related challenges regarding data use. As with any kind of decision making, AI-based choices are only as good as the information on which they rely.
Integrating AI into regulation is a big challenge that brings substantial risks, but the cost of sticking with largely analog systems is greater.
Accordingly, regulators face tremendous challenges regarding how to receive and clean data. AI can deal most easily with “structured data,” which arrives in organized formats and fields that the algorithm easily recognizes and puts to use. With NLP tools, AI can also make sense of “unstructured data.” Being sure, however, that the AI is using accurate data and understanding it requires a great deal of work. Uses of AI in finance will require ironclad methods for ensuring that data is collected and “cleaned” properly before it undergoes algorithmic analysis. The old statistics maxim “garbage in, garbage out” becomes even more urgent when the statistical analysis will be done by machines using methods that its human minders cannot fully grasp.
It is critical that policymakers focus on what is at stake. AI that might be good at, say, recommending a movie to watch on Netflix will not suffice for deciding whether to approve someone for a mortgage or a small-business loan or let them open a bank account.
Data protection and privacy: Widespread use of AI will also necessitate deep policy work on the ethics and practicalities of using data. What kinds of information should be used and what should be off-limits? How will it be protected from security risks and government misuse? Should people have the right to force-remove past online data, and should companies’ encryption techniques be impenetrable even by the government?
Privacy-enhancing technologies may be able to mitigate these risks, but the dangers will require permanent vigilance. The challenge will spike even higher with the approach of quantum computing that has the power to break the encryption techniques used to keep data safe.
Model Risk Management (MRM): Mathematical models are already widely used in financial services and financial regulation. They raise challenges that will only grow as AI becomes more widely employed. This is particularly true as AI is placed in the hands of people who do not understand how it makes decisions. Regulators and industry alike will need clear governance protocols to ensure that these AI tools are frequently retested, built on sufficiently robust and accurate data, and are kept up to date in both their data and technical foundations.
 AI roadmap for regulators
AI roadmap for regulators
Redesigning financial regulation to catch up to the acceleration of AI and other industry innovation is somewhat analogous to the shift in cameras from analog to digital at the turn of the millennium. An analog camera produces an image in a form that is cumbersome, requiring expert (and expensive) manipulation to edit photos. Improving the process of taking pictures with 35-millimeter film hits a ceiling at a certain point. By comparison, the digital or smartphone camera was a whole new paradigm, converting images into digital information that could be copied, printed, subjected to artificial intelligence for archiving and other methods, and incorporated into other media. The digital camera was not an evolution of the analog version that preceded it. It was entirely different technology.
Similarly, current regulatory technologies are built on top of an underlying system of information and processes that were all originally designed on paper. As a result, they are built around the constraining assumptions of the analog era, namely that information is scarce and expensive to obtain, and so is computing power.
To undertake a more dramatic shift to a digitally native design, regulators should create new “taxonomies” of their requirements (which some agencies are already developing) that can be mapped to AI-powered machines. They should also develop comprehensive education programs to train their personnel in technology knowledge and skills, including baseline training on core topics, of which AI is a single, integral part. Other key “big data” issues include the Internet of Things, cloud computing, open source code, blockchains and distributed ledger technology, cryptography, quantum computing, Application Program Interfaces (APIs), robotic process automation (RPI), privacy enhancing technologies (PETs), Software as a Service (Saas), agile workflow, and human-centered design.
These are big challenges that bring substantial risks, but the cost of sticking with largely analog systems is greater. Personnel may fear that such an overhaul could result in machines taking their jobs, or that machines will make catastrophic errors, resulting in financial mishaps. On the former fear, robotics and AI can in fact empower human beings to do their jobs better, by decreasing vast amounts of routine work duties and freeing up people to use their uniquely human skills on high-value objectives. On the second fear, agencies should build cultures grounded in an understanding that humans should not cede significant decisionmaking to machines. Rather, experts should use technology to help prioritize their own efforts and enhance their work.
Data is the new oil not only in its value but in its impact: Like oil, digitization of data can solve some problems and cause others. The key to achieving optimal outcomes is to use both data and AI in thoughtful ways—carefully designing new systems to prevent harm, while seizing on AI’s ability to analyze volumes of information that would overwhelm traditional methods of analysis. A digitally robust regulatory system with AI at its core can equip regulators to solve real-world problems, while showcasing how technology can be used for good in the financial system and beyond.
The author serves on the board of directors of FinRegLab, a nonprofit organization whose research includes a focus on use of AI in financial regulatory matters. She did not receive financial support from any firm or person for this article or from any firm or person with a financial or political interest in this article. Other than the aforementioned, the author is not currently an officer, director, or board member of any organization with a financial or political interest in this article.
Looking for an article from a previous week? Visit the NASCUS Digital Article Repository. Further information can be found in the Digital Library, under News & Analysis in the top navigation.
May 19, 2022 Feature: “Run-like” Risk and Policy Proposals Noted in the Congressional Research Service Report on the TerraUSD Crash
 May 16, 2022 — The Congressional Research Service (CRS), a legislative agency that supports the United States Congress, has published a report(posted below) that outlines algorithmic stable coins and key factors within the TerraUSD (UST) crash. CRS describes the UST crash as a “run-like” scenario along with policy issues connected to the risk of such events.
May 16, 2022 — The Congressional Research Service (CRS), a legislative agency that supports the United States Congress, has published a report(posted below) that outlines algorithmic stable coins and key factors within the TerraUSD (UST) crash. CRS describes the UST crash as a “run-like” scenario along with policy issues connected to the risk of such events.
Related Reading links/summaries below. These links cover efforts in crypto regulation legislation, lobbying efforts, and the SEC increasing “Crypto Cops” to fight digital fraud.
What Are Algorithmic Stablecoins?
Stablecoins are a type of cryptocurrency that aim to maintain a stable value. There are several classes of stablecoins that each use different methods to try to achieve this, one of which is algorithmic stablecoins. While no precise definition captures all of their features, algorithmic stablecoins typically use an algorithm or smart contract to manage the supply of tokens and guide their value to some reference asset (for example a fiat currency, such as the U.S. dollar). Algorithmic stablecoins generally do not attempt to achieve value by holding a reserve of fiat-denominated assets with a value in a 1:1 relationship with the value of the stablecoin. Instead, algorithmic stablecoins use different mechanisms to control the supply or value of the stablecoin, including the minting or burning of coins, rebasing, and arbitrage.
What Happened with TerraUSD?
TerraUSD (UST) stablecoin uses an arbitrage mechanism typical of some algorithmic stablecoin arrangements consisting of two coins or tokens: the stablecoin, in this case UST, meant to maintain a stable value or “peg,” and a balancer token, in this case,LUNA, the value of which can fluctuate. An algorithm manages the relationship between these two coins to attempt keeping the stablecoin pegged to the reference. If strong demand pushed the price of UST above its peg, arbitrageurs could buy $1 worth of LUNA, trade it for 1 UST (worth more than $1) and sell UST for a gain. If UST falls below $1, someone can buy $0.99 worth of UST and trade it for $1 worth of LUNA. In both instances arbitrageurs net a profit and ostensibly maintain the peg.
Over the past week, UST lost its peg to the dollar (Figure 1), and both UST and balancer coin LUNA were dropped from various cryptocurrency exchanges. UST hit a low of $0.12 at 9 a.m. on May 16, 2022.
Source: CoinMarketCap.
There are two other factors relevant to this incident.
First, Terraform Labs, the UST stablecoin manager, established Anchor, a decentralized lending protocol in which UST holders could park their UST for a reported 20% annual percentage yield. This protocol attracted demand for UST because of high yields. However, Anchor experienced sizeable UST withdrawals late last week foreshadowing the depegging. Also, in early 2022, Terraform Labs began purchasing bitcoin to hold in the Luna Foundation Guard (LFG) in response to some concerns about the peg. The LFG could sell bitcoin to prop up the stablecoin and defend the peg, which it claims to have done during the selloff but about which there is some skepticism.
Policy Issues Relating to the “Run” Risk
UST had a market capitalization of more than $18 billion in early May. Some observers voiced financial stability concerns because of UST’s contagion effects on other crypto assets and the crypto ecosystem’s interconnectedness with the traditional financial system. The sudden drop in UST’s prices reflects a classic “run-like” scenario, where a large number of investors withdraw their investments simultaneously, triggering negative feedback loops and contagion effects.
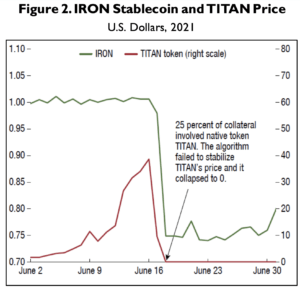
Global Financial Stability Report
Some argue that stablecoins could be subject to runs if coin holders have suspicions about the reserve assets backing the par value. The run-like behaviors already occurred for algorithmic stablecoins during relatively calm market conditions. In contrast, vulnerabilities like this are generally expected to possibly cascade and become more influential during broader market distress.
The UST event is not the first time an algorithmic stablecoin displayed run-like behavior. The Iron Titanium (TITAN) token faced a run-like scenario in June 2021 and saw its price crash to near zero within one day. Similar to how UST functions with LUNA, the algorithmic stablecoin Iron is partially supported by TITAN. Because Iron is structured using TITAN and USD Coin, when TITAN’s price collapsed, Iron was trading off the peg by more than a quarter (Figure 2).
Many observers consider the stablecoin industry as not adequately regulated. While in the traditional financial system, a run-like scenario could be somewhat mitigated by regulatory safeguards and backstops, the stablecoin industry has not incorporated such measures. For example, in the traditional financial system, bank deposit insurance and liquidity facilities could reduce market participants’ incentives to have a run. For more background, see CRS products on Stablecoins: Background and PolicyIssues and How Stable Are Stablecoins?
Policy Proposals
Recent legislative proposals have considered what entities should be allowed to issue stablecoins, the reserves needed to back a stablecoin, and the disclosures that stablecoin issuers should have to make available. Committees in both the Senate and House have held hearings on stablecoins where the reserves backing these digital assets were a central issue.
With respect to reserve disclosure and composition, there have been a few recent legislative proposals. In March 2022, Representative Hollingsworth introduced H.R. 7328, which would establish auditor-verified reporting requirements for stablecoin issuers and restrict the assets that could back a stablecoin. Senator Hagerty introduced a Senate version of the bill, S. 3970, in May 2022. There have also been some discussion drafts in the House and Senate. These discussion bills provide a possible framework for stablecoin issuers. For example, while these drafts differ in their approach, they would establish institutions eligible to issue stablecoins, create disclosure requirements for the assets backing stablecoin, provide standards for the composition of those reserves, and consider avenues for financial backstops for stablecoins.
Regulators have also taken measures to address the risks associated with stablecoins. For example, in addition to the President’s Working Group report on stablecoins, the banking regulators have jointly participated in “policy sprints” focused on crypto assets, including stablecoins. Additionally, last year, the Basel Committee on Banking Supervision released a consultative document on prudential treatment of crypto exposures for public comment, and they are expected to finalize their consultative framework this year. The Department of the Treasury is reportedly working on a report on TerraUSD.
![]() Related Readings:
Related Readings:
- Cryptocurrencies Melt Down in a ‘Perfect Storm’ of Fear and Panic: A steep sell-off that gained momentum this week starkly illustrated the risks of the experimental and unregulated digital currencies.
The price of Bitcoin plunged to its lowest point since 2020. Coinbase, the large cryptocurrency exchange, tanked in value. A cryptocurrency that promoted itself as a stable means of exchange collapsed. And more than $300 billion was wiped out by a crash in cryptocurrency prices since Monday. The crypto world went into a full meltdown this week in a sell-off that graphically illustrated the risks of the experimental and unregulated digital currencies. - U.S. Senate Crafting Crypto Regulatory Legislation
A bipartisan group of U.S. senators plans to release a long-sought framework for regulating the volatile cryptocurrency market next week amid signs of market chaos. The group will release the draft for public comment and introduce a formal bill as soon as 30 days afterward, according to Sen. Cynthia Lummis (R-WY), who said she will sponsor the legislation along with Sen. Kirsten Gillibrand (D-NY) and several other senators, joining at least one other crypto bill floating around the Senate, that one introduced by Sen. Pat Toomey (R-PA). - U.S. Crypto Lobbyists in Push to Contain Fallout from Stablecoin Meltdown
The Blockchain Association and the Chamber of Digital Commerce, which represent some of the most influential crypto companies, say they have been fielding a flurry of questions from Capitol Hill since TerraUSD, known as “UST,” broke its peg last week and crashed 90%. Capitol Hill lawmakers have been quizzing lobbyists on the structure of UST, seeking to determine whether its collapse was preventable and if other stablecoins could suffer the same fate. - SEC to Hire More Cryptocurrency Cops to Fight Digital FraudsThe Securities and Exchange Commission will boost the size of its special unit devoted to investigating cryptocurrency frauds and other misconduct, a move that follows the agency’s aggressive push to get the unregulated industry to come under federal supervision. The commission has positioned itself as the chief government bulwark against fraud in the $1.7 trillion market, which so far has sidestepped most federal consumer- and investor-protection rules. SEC Chairman Gary Gensler says the crypto industry is rife with fraud and abuse, likening it to the “Wild West.”
