Oct. 24, 2022 — The Federal Housing Finance Agency (FHFA) today published its new Uniform Appraisal Dataset (UAD) Aggregate Statistics Data File. FHFA also launched UAD Aggregate Statistics Dashboards on its website to provide user-friendly visualizations of the newly available data.
Oct. 24, 2022 — The Federal Housing Finance Agency (FHFA) today published its new Uniform Appraisal Dataset (UAD) Aggregate Statistics Data File. FHFA also launched UAD Aggregate Statistics Dashboards on its website to provide user-friendly visualizations of the newly available data.
“As home valuations are a vital component of the mortgage process, publishing transparent, aggregate data on appraisals provides useful information to the public while protecting borrowers’ personally identifiable information,” said Director Sandra L. Thompson. “Today’s announcement exemplifies our commitment to the development of a more efficient and equitable valuation system that ultimately reduces appraisal bias.”
The UAD Aggregate Statistics Data File and UAD Aggregate Statistics Dashboards give stakeholders and the public new access to a broad set of data points and trends found in appraisal reports. Additionally, the appraisal statistics may be grouped by neighborhood characteristics and geographic levels (national, state plus the District of Columbia and Puerto Rico, Metropolitan Statistical Areas (MSAs) or Metropolitan Divisions, county, and tract). Of note, the UAD Aggregate Statistics Data File is intended for users capable of using statistical software to extract and analyze data. In contrast, the UAD Aggregate Statistics Dashboards are for users of all types and are designed to provide user-friendly access through customized maps and charts.
FHFA’s Division of Research and Statistics used 47.3 million UAD appraisal records collected from 2013 through the second quarter of 2022 on single-family properties to create a data file of UAD aggregate statistics in a manner that protects borrower privacy. Each UAD appraisal record includes information reported by appraisers on the Uniform Residential Appraisal Report (URAR). The current version of the URAR for single-family homes is Fannie Mae Form 1004 and Freddie Mac Form 70.
Related Links:
- UAD Aggregate Statistics Dashboards
- UAD Aggregate Statistics Data File
- UAD Aggregate Statistics Blog
Compliance professionals within financial service firms are finding that they need to demonstrate their abilities with new technologies in order to meet regulatory requirements
The expansion of governance, risk, and compliance responsibilities into new technology-related areas beyond traditional functions has created a new burden for financial service firms’ compliance departments, and placed new demands on the skills of compliance professionals.
The intersection of compliance with tech has created a need for expertise and essential coordination across firms while involving artificial intelligence, big data, data privacy, cybersecurity, and algorithmic trading, to name just a few.
Financial service firms must now fully integrate these technologies and demonstrate that the activities employing them meet regulatory requirements. For compliance professionals, it has become essential to understand how the technologies work as well as their limitations and vulnerabilities. It can even help to know the computer code that went into creating them.
Several recent enforcement cases and regulatory initiatives underscore the need for compliance departments to become more tech savvy by taking steps that include technical coordination across the company, embedding technologists within compliance teams, or increasing the tech skills of individual compliance professionals.
DOJ emphasis on data
Deputy Attorney General Lisa Monaco gave a speech last month outlining ambitious plans being embraced by the Department of Justice (DOJ) to fight corporate misconduct. Among the principles, there was significant emphasis placed on the need to demonstrate an overall compliance culture.
The DOJ made clear in its compliance program guidelines released in 2020 that prosecutors should evaluate whether companies have a “data-driven compliance program” to detect potential misconduct and to monitor the effectiveness of their compliance policies. Monaco expanded on that in her speech and in an accompanying memo to federal prosecutors.
In evaluating whether a compliance program is “adequately resourced and empowered,” the DOJ said in 2020, prosecutors should consider the following questions:
“Do compliance and control personnel have sufficient direct or indirect access to relevant sources of data to allow for timely and effective monitoring and/or testing of policies, controls and transactions? Do any impediments exist that limit access to relevant sources of data and, if so, what is the company doing to address the impediments?”
The emphasis on “access” to data can be viewed as a signal that the DOJ needs to see people with skills in place to analyze, monitor, and interpret such data on the part of compliance departments.
Regulators emphasis on monitoring communications
The new policies put forth in Monaco’s memo also focus on monitoring the use of personal devices and third-party messaging platforms — a demanding technology task. “The ubiquity of personal smartphones, tablets, laptops, and other devices poses significant corporate compliance risks, particularly as to the ability of companies to monitor the use of such devices for misconduct and to recover relevant data from them during a subsequent investigation,” the memo stated. “The rise in use of third-party messaging platforms, including the use of ephemeral and encrypted messaging applications, poses a similar challenge.”
Other financial regulators have pursued similar priorities. In December last year, JPMorgan Chase & Co.’s securities unit was slapped with a $200 million penalty over data retention violations related to the use of personal communications and messaging devices. The Securities and Exchange Commission (SEC) imposed a $125 million share of the fine, and the Commodity Futures Trading Commission (CFTC) claimed the remaining $75 million.
The JPMorgan case represented the largest-ever fine for record-keeping violations related to communications reviews. It was followed up last week with an announcement by the SEC and CFTC of similar case settlements involving 16 other large financial institutions, which were fined $1.1 billion and $710 million by the agencies, respectively.
In the release announcing the settlements, the SEC said employees of the penalized firms had routinely communicated about business matters using text messaging applications on their personal devices. “The firms did not maintain or preserve the substantial majority of these off-channel communications, in violation of the federal securities laws,” the SEC stated. “The failings occurred across all of the 16 firms and involved employees at multiple levels of authority, including supervisors and senior executives.”
Compliance takeaways
The rapidly changing and growing compliance, risk, and audit responsibilities stemming from technology innovation require compliance departments to examine their own expertise, capabilities, and skill requirements.
The 2022 Cost of Compliance Survey, published by Thomson Reuters Regulatory Intelligence, showed frustration that, despite compliance departments’ widening responsibilities, staff numbers are unlikely to grow as staff costs increase and financial service firm budgets remain tight. Therefore, outsourcing, technology, and regulatory technology may step in to plug some of the gaps. Still, there will be a growing need for compliance professionals within firms to become more sophisticated in order to better steer the type of changes required by the new technologies.
As the Compliance Survey noted: “Of the 66% of respondents who expect the cost of senior compliance staff to increase in the next 12 months, nearly half (47%) gave the demand for skilled staff and knowledge as the top reason.”
Although the use of outsourcing and third-party management has been a popular strategy for many firms due to the complexities of software development, cloud computing, and data privacy and storage, regulators still expect compliance departments to have a thorough understanding and knowledge to oversee and “own” these outsourced functions.
Courtesy of Todd Ehret, Senior Regulatory Intelligence Expert, ThomsonReuters
Please join Consumer Financial Services Partner Chris Willis and his colleague and fellow Partner Jordi de Llano as they discuss recent developments in anti-money laundering. In this episode, the attorneys examine FinCen’s September 2022 final rule, which implements guidance on new beneficial ownership information reporting requirements of the Corporate Transparency Act (CTA), as well as take a deeper dive into recent developments and what it means for different entities.
Jordi de Llano formerly served as assistant U.S. attorney and deputy chief of the Securities, Financial, and Cyber Fraud Unit in the U.S. attorney’s office in Boston. He also previously ran the Financial Crimes/Suspicious Activity Report (SAR) Review Task Force at the U.S. attorney’s office in Lexington, KY. In that role, Jordi oversaw all investigations involving SARs, Bank Secrecy Act (BSA) violations, and money laundering. He also served as the primary liaison for the U.S. attorney’s office with local financial institutions regarding BSA compliance issues. With nearly a decade of experience as a seasoned federal prosecutor managing complex financial investigations, Jordi now focuses on representing corporate and individual clients facing criminal cases and government investigations.
Courtesy of Troutman Pepper
 Globally, over half of the passwords are reused, exposing personal and corporate data at risk.
Globally, over half of the passwords are reused, exposing personal and corporate data at risk.
After analyzing hundreds of millions of anonymous data points, privacy firm Dashlane released a report on password health.
The average password health score globally falls within the “needs improvement” range, meaning that passwords might be weak, compromised, or reused.
In fact, the report found that globally 51% of passwords are reused. An average person in the US has 70-80 online accounts, so one compromised password could lead to dozens of hacked accounts.
What is more, nearly 20% of passwords are compromised. Dashlane considers it an incredibly high number, given that an average Dashlane user has around 240 online accounts.
“Passwords are often the weak link in an organization’s or individual’s cybersecurity — in fact, for Basic Web Application Attacks (BWAA), over 80% of breaches can be attributed to stolen credentials,” the report reads.
The company warned that the number of online accounts per person is growing, so password security should be an essential part of an organization’s cybersecurity strategy.
How to protect yourself
If you can remember your password, consider it weak.
“Use unique generated passwords that you cannot pronounce yourself. Another crucial thing is to use multifactor authentication whenever possible. So even if your accounts get breached, you will still have this additional layer of security,” Gediminas Brencius, Head of Product for NordPass, once told Cybernews.
He also suggested using compartments for your information. If you have many different social accounts, you should use a specific email address for those.
Cybernews researchers have also documented the most commonly used passwords. If you noticed that your own personal passwords have similar patterns to the ones we analyzed, we recommend you visit our Data Leak Checker to see if your email address and other personal data has been exposed in a data breach.
And if you don’t want to end up on that list – the largest database of known breached accounts, with more than 15 billion compromised accounts – we also recommend using password managers.
Courtesy of Jurgita Lapienytė, CyberNews.com
 Oct. 20, 2022 – The National Credit Union Administration Board held its ninth open meeting—and second in person—of 2022, and approved the agency’s Enterprise Risk Appetite Statement, which helps the agency align risks and opportunities when making decisions and allocating resources to achieve the agency’s strategic goals and objectives.
Oct. 20, 2022 – The National Credit Union Administration Board held its ninth open meeting—and second in person—of 2022, and approved the agency’s Enterprise Risk Appetite Statement, which helps the agency align risks and opportunities when making decisions and allocating resources to achieve the agency’s strategic goals and objectives.
The NCUA Board was also briefed on the state of the Central Liquidity Facility (CLF) and cybersecurity trends affecting federally insured credit unions and the broader financial system.
Read the remarks by the NCUA Board Members Here
Board Approves New Enterprise Risk Appetite Statement
The NCUA Board unanimously approved the NCUA’s new enterprise risk appetite statement prepared by the agency’s Enterprise Risk Management Council. The statement is a management tool that provides guidance from agency leadership to managers and staff on the amount of risk the NCUA is willing to undertake in pursuit of its objectives.
“The enterprise risk appetite statement presented today is part of the NCUA’s overall management approach. And, I am especially pleased that we will have an averse risk appetite when addressing identified safety and soundness concerns at credit unions,” NCUA Chairman Todd M. Harper said. “This means we will be risk-focused and ready to act expeditiously if needed. I also appreciate that through this statement we will remain focused on ensuring compliance with and enforcement of federal consumer financial protection laws and regulations at credit unions.”
The NCUA’s Enterprise Risk Management Council developed a risk appetite statement through careful consideration and evaluation of the risks the agency faces and focused on achieving several programmatic goals, which included:
- Communicating guidelines about the levels of risk the NCUA is willing to accept in pursuit of its mission and goals;
- Promoting consistency in understanding, measuring, and managing risk across the enterprise;
- Informing agency responses to risks and decision-making to balance limited time and resources; and
- Driving a more risk-aware culture.
Briefing Highlights Central Liquidity Fund’s Status for 3rd Quarter
The Central Liquidity Facility President briefed the NCUA Board on the status of the Central Liquidity Fund as of September 30, 2022. The briefing covered liquidity and contingency funding plans, liquidity sources and needs, CLF advances, and membership requirements. The CLF president also discussed enhancements to the CLF’s processes and structures to ensure it can serve as an effective liquidity backstop for the credit union system should the need arise.
Said Chairman Harper, “The CLF is a vital source of emergency liquidity within the credit union system. However, the pending expiration of the temporary CLF enhancements authorized by Congress at the start of the COVID-19 pandemic remains a very real concern. While we are grateful to Congress for allowing the CLF enhancements of the last few years, there is a real need to keep in place the ability of corporate credit unions to serve as a CLF agent for a subset of their members. That authority will allow us to provide emergency liquidity quickly when needed.”
Financial highlights for the CLF in the third quarter include:
- $1.243 billion in total assets;
- $1.1 million in year-to-date net income;
- $40.5 million in retained earnings;
- 2.24 percent dividend was paid to members of the CLF in the third quarter;
- 3,991 corporate credit unions and consumer credit unions have access to the CLF; and
- $29.1 billion in borrowing authority for the CLF.
The Central Liquidity Facility is an NCUA-operated, mixed-ownership government corporation that was created to improve the general financial stability of credit unions by serving as a liquidity lender to credit unions experiencing unusual or unexpected liquidity shortfalls. Member credit unions own the CLF, which exists within the NCUA. The CLF’s President manages the facility under the oversight of the NCUA Board.
Cybersecurity Threats Continue, NCUA Launches ISE Program at Year-end
Ransomware, cloud migration, and distributed denial-of-service attacks are contributing to a dynamic threat landscape that creates evolving risks for federally insured credit unions, according to a briefing provided to the NCUA Board by the agency’s Critical Infrastructure Division. Additionally, rising geopolitical tensions continue to increase the potential for cyberattacks on the financial system and other parts of the nation’s critical infrastructure.
“Each of us — the NCUA, state supervisory authorities, vendors, and credit unions — has a responsibility to protect our systems, improve our ability to recover from incidents, educate our teams, share information, and report and address potential vulnerabilities,” Chairman Harper said. “Our chain is only as strong as our weakest link, so we all must be hypervigilant to prevent a catastrophic failure.”
The briefing also outlined good cyber hygiene practices, summarized the NCUA’s proposed cyber incident reporting rule, and provided an update on the NCUA’s Information Security Examination (ISE) Program. This new examination program offers flexibility for credit unions of all asset sizes and complexity levels while providing examiners with standardized review steps to facilitate advanced data collection and analysis. These new examination procedures will assist the credit union system in preparing for, withstanding, and recovering from cybersecurity threats. The ISE examination procedures will be deployed at the end of 2022.
The NCUA strongly encourages credit unions to strengthen their cybersecurity programs and preparedness and immediately report known details of cyber incidents to the NCUA, the FBI, and the Cybersecurity and Infrastructure Security Agency.
Credit unions are also encouraged to download and use the NCUA’s Automated Cybersecurity Evaluation Toolbox, or ACET. The ACET is an excellent resource for small credit unions or those credit unions with limited resources to take the first steps in understanding their level of cyber preparedness. Additional cyber-related information and resources are available on the NCUA’s cybersecurity resources webpage.
October 13, 2022 — The Federal Reserve Board and the Consumer Financial Protection Bureau today announced the dollar thresholds used to determine whether certain consumer credit and lease transactions in 2023 are exempt from Regulation Z (Truth in Lending) and Regulation M (Consumer Leasing).
By law, the agencies are required to adjust the thresholds annually based on the annual percentage increase in the Consumer Price Index for Urban Wage Earners and Clerical Workers, known as CPI-W. Transactions at or below the thresholds are subject to the protections of the regulations.
Specifically, based on the annual percentage increase in the CPI-W as of June 1, 2022, Regulation Z and Regulation M generally will apply to consumer credit transactions and consumer leases of $66,400 or less in 2023. However, private education loans and loans secured by real property, such as mortgages, are subject to Regulation Z regardless of the amount of the loan.
Read the Consumer Leasing (Regulation M).
Read the Truth in Lending (Regulation Z).
Questions for the Federal Reserve Board can be directed to Laura Benedict at [email protected] or (202) 452-2955.
Oct. 12, 2022 — New data reveals that nearly half of Americans (46%) are in credit card debt, with the average debt being $6,093. The findings are based on a survey of 1,001 Americans by Anytime Estimate, a unit of Clever Real estate.
The numbers are even more important given a rising rate environment, meaning the cost of that debt is going to grow, and the potential for a recession. The survey found that even two-thirds of those without credit card debt (66%) worry current conditions could soon have them falling behind on card payments.
The Findings
Among the findings:
- Of those in credit card debt, the average Baby Boomer ($8,208) owes more than the average Millennial ($6,182) and Gen Zer ($3,196).
- 76% of respondents have had credit card debt at some point in their lives.
- 1 in 8 Americans have missed a credit card payment in 2022.
- Millennials are four times more likely than Baby Boomers to report missing a payment in 2022 (13% vs. 3%).
- 35% of Americans have missed a credit card payment in the last five years.
- Half of Americans who have missed a credit card payment (50%) did so to afford basic living expenses, such as food, housing, or utilities.
- 80% of Americans with credit card debt are also in some other form of debt.
- Americans rank credit card debt as their most stressful form of debt — above medical debt, mortgage debt, and student loan debt.
- 27% of Americans don’t know their credit card interest rate, and 37% say they’ve opened a new credit card without prior research.
- About 1 in 3 Americans (31%) have had their credit card information stolen.
- The average credit card user spends $1,579 on their cards per month, with about 1 in 8 users (12%) spending over $5,000 per month.
- 1 in 3 Americans couldn’t cover a $2,000 emergency bill
The full analysis can be found here.
Reimbursing cyber scams
As banks are under pressure to compensate their scammed consumers, rising cybercrime rates translate to rising costs for the industry. More than half (58%) of those who conduct their banking online encounter scams via email or SMS at least once per week, and 23% report having fallen victim to a cyberattack.
Banks currently reimburse authorized push payment (APP) fraud at an average rate of 46%. Although many banking institutions are refusing reimbursements for online fraud, this is due to change soon, or else the situation will backfire. For example, measures supported by the UK government will require banks to reimburse everyone. This is only one illustration of the fact that if banks are to secure their consumers and their business line in 2022, they must prioritize cybersecurity more highly.
To exchange efficient strategies, banks will need to collaborate with governments and industry organizations. The public must continue to get education on preventative measures, but ultimately it is the banks’ responsibility to establish security models that will give them and their clients the greatest level of safety.
Maintain compliance with strict privacy regulations
The use of social engineering and account takeover fraud will increase over the next years. Financial institutions must not only conduct comprehensive data checks beyond document verification at account opening to fight this but also keep track of customer identities throughout the customer lifecycle.
Banks must decide how to manage sensitive personal data like biometrics as GDPR and other privacy regulations are being established throughout the world. As a result, many institutions believe that finding a partner that can protect this sensitive personal information is more practical than modernizing internal systems and processes.
Finally, the public is becoming more concerned about how technology corporations utilize personal data. More difficult questions will be raised as a result, and any responses must pass a strict ethical standard. The application of AI to compliance and fraud will need to be explained by banks. Ascertaining whether their partners and vendors have complete control over the technology they provide will also have an impact on vendor onboarding. Every bank will need to be able to justify decisions made to regulators and the broader public.
Leveraging AI to combat cyber fraud
Instead of being a subset of financial crime, banking fraud now coexists with ransomware, phishing, and other types of cybercrime. Fraudsters are functioning methodically, getting more skilled at spotting loopholes in the automated systems that financial institutions are putting in place, and getting better at learning through repetition.
For example, banks and mortgage lenders have started to link more of their fraud charges to the fact that their clients are doing more transactions using mobile banking apps. According to a LexisNexis survey, more than half of the respondents who worked for US banks and credit lenders say that mobile channel fraud has increased by 10% or more this year.
Today’s fraudsters collaborate with criminal gangs that provide crime as a service. As a result, frauds and forgeries become increasingly sophisticated, making them impossible for humans to detect without artificial intelligence (AI) to support their decision-making.
Decentralized currencies are at the center of attacks
Meanwhile, cryptocurrency has become a primary target of cyberattacks. Huge sums of money are frequently present on cryptocurrency exchanges and wallets, making them a powerful attraction for attackers trying to make money from their attacks.
These are sometimes straightforward social engineering attacks, and other times they are far more sophisticated technically. We expect to see more cyberattacks on decentralized currencies given the amount of money that can be stolen in a single successful attack (possibly reaching millions of dollars). For example, in December 2021 criminals stole nearly $200 million from the crypto trading platform Bitmart.
However, we should anticipate law enforcement and governments to become more actively involved in both the investigation of cryptocurrency assaults and the use of cryptocurrency vulnerabilities. For example, government agencies like the Securities Exchange Commission (SEC) and Commodity Futures Trading Commission (CFTC) may try to regulate cryptocurrencies more strictly as they regulate traditional currencies.
Attacks bypassing MFA
Although multi-factor authentication is a prerequisite for enabling strong customer authentication, the latest attacks against Cisco and Uber have profoundly demonstrated that fraudsters can bypass MFA. Using sophisticated tactics and tools like auto-diallers, criminals have managed to intercept one-time passwords (OTP) and compromise banking accounts. Automating the process and creating what is known as MFA fatigue they force customers to give up OTPs to malicious bots.
OTP interception is now trivial compared to what it has been historically, and that innovation fundamentally shifts the economics in the favor of the attackers. The LexisNexis report highlighted this concern saying that balancing fraud detection with customer friction is a top challenge for banks. Banks need to embrace phishing-resistant MFA methods that eliminate the risk of being defrauded while offering a superb customer experience for all possible use cases and authentication journeys.
A bigger attack surface and higher attack sophistication levels are a result of the rising use of complicated technologies and interaction with third-party systems. Today, maintaining a strong cybersecurity posture entails more than merely defending sensitive systems and data from damaging external attacks. Additionally, it entails better data privacy, identity protection, and vulnerability management. Banks and financial institutions can outsource part of the burden of staying compliant with regulations and securing customer financial data by partnering with a trusted managed services provider. These companies aggregate experience and expertise to help banking institutions stay one step ahead of their adversaries.
CFPB Weighs in on Data Security; Will Firms with Poor Security Be in the Crosshairs?
Friday, October 14, 2022 | 1:00 – 2:00 p.m. ET
There is no cost for this webinar.
Program Description
In the late summer, the Consumer Financial Protection Bureau (CFPB) issued a circular that concluded in no uncertain terms that insufficient data protection or information security could be considered an unfair practice under the Consumer Financial Protection Act. Circulars are general statements of policy circulated to other agencies, state and federal, that have overlapping authority with the CFPB to enforce federal consumer financial law, such as the Federal Trade Commission (FTC), Department of Justice, and state attorneys general, to name a few.
The CFPB specifically called out the need to implement specific “cost-efficient measures to protect consumer data”: multi-factor authentication, password management, and timely software updates. Additionally, the new Safeguards Rule enforced by the FTC remains the primary federal source of affirmative requirements for nonbanks. Join lawyers from Venable’s Financial Services Group and cybersecurity experts from the firm’s Cybersecurity Risk Management Group for a webinar that will discuss the impact of this circular and provide a primer on data security measures companies that collect and use consumer data should adopt or enhance.
For more information contact: [email protected]
Speakers
- Andrew E. Bigart, Partner, Venable LLP
- Jeremy A. Grant, Managing Director of Technology Business Strategy, Venable LLP
- Alexandra Megaris, Partner, Venable LLP
- Ross B. Nodurft, Senior Director of Cybersecurity Services, Venable LLP
CLE Accreditation
This activity has been approved for Minimum Continuing Legal Education credit by the State Bar of California in the amount of one hour, of which one hour applies to the general credit requirement, by the State Bar of New York in the amount of one credit hour, of which one credit hour can be applied toward the areas of professional practice credit requirement, and by the MCLE Board of the Supreme Court of Illinois in the amount of one credit hour, of which one credit hour can be applied toward the general credit requirement. Venable certifies this activity conforms to the standards for approved education activities prescribed by the rules and regulations of the State Bar of California, State Bar of New York, and MCLE Board of the Supreme Court of Illinois, which govern minimum continuing legal education. Venable is a State Bar of California, State Bar of New York, and MCLE Board of the Supreme Court of Illinois accredited MCLE provider. This program is appropriate for both experienced and newly admitted attorneys.
For more information on CLE accreditation, please click here.
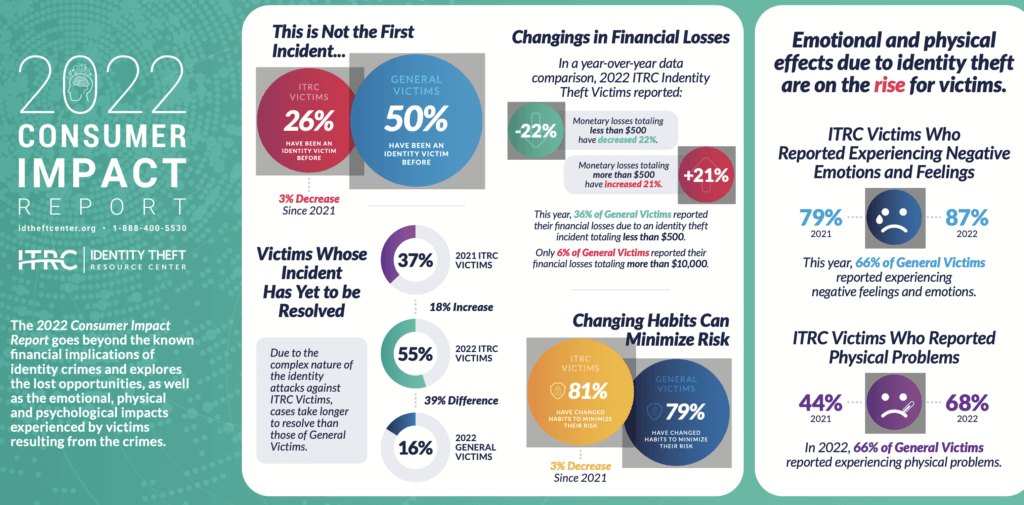
About the ITRC Consumer Impact Report
Since 2003, the ITRC has surveyed the identity crime victims who have contacted the Center to gauge the impact of identity compromises on individuals. Numerous studies by government agencies and private organizations focus on the financial impacts of identity-related crimes. However, the primary purpose of the ITRC Consumer Impact Report is to gauge the emotional, physical and practical effects on the day-to-day lives of victims, including lost opportunities.
This year’s report reflects the responses of 120 victims who contacted the ITRC between April 2021 and March 2022. In the time period covered by this report, new forms of identity attacks emerged. Social media account take-over grew by more than 1,000 percent in just one year. We sought additional input, specifically from victims whose social media accounts were compromised. This survey includes the responses of 97 victims who contacted the ITRC and shows the impacts of the loss of access to a social media account are more significant than first believed.
Previous Consumer Impact Reports dating back to 2003 only reflected the experience of victims who contacted the ITRC. To get a broader view of the trends and impacts affecting consumers in general, this year, the ITRC asked 1,371 consumers in an online survey if they had been the victim of an identity crime and, if so, how it impacted them. Responses from this broader set of self-identified victims using similar questions asked of victims who contacted the ITRC show both significant differences and common experiences.
October 05, 2022 — The Federal Bureau of Investigation (FBI) and CISA have published a joint public service announcement that:
- Assesses malicious cyber activity aiming to compromise election infrastructure is unlikely to result in large-scale disruptions or prevent voting.
- Confirms “the FBI and CISA have no reporting to suggest cyber activity has ever prevented a registered voter from casting a ballot, compromised the integrity of any ballots cast, or affected the accuracy of voter registration information.”
The PSA also describes the extensive safeguards in place to protect election infrastructure and includes recommendations for protecting against election-related cyber threats.
Malicious Cyber Activity Against Election Infrastructure Unlikely to Disrupt or Prevent Voting
 The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) assess that any attempts by cyber actors to compromise election infrastructure are unlikely to result in large- scale disruptions or prevent voting. As of the date of this report, the FBI and CISA have no reporting to suggest cyber activity has ever prevented a registered voter from casting a ballot, compromised the integrity of any ballots cast, or affected the accuracy of voter registration information. Any attempts tracked by FBI and CISA have remained localized and were blocked or successfully mitigated with minimal or no disruption to election processes.
The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) assess that any attempts by cyber actors to compromise election infrastructure are unlikely to result in large- scale disruptions or prevent voting. As of the date of this report, the FBI and CISA have no reporting to suggest cyber activity has ever prevented a registered voter from casting a ballot, compromised the integrity of any ballots cast, or affected the accuracy of voter registration information. Any attempts tracked by FBI and CISA have remained localized and were blocked or successfully mitigated with minimal or no disruption to election processes.
 The public should be aware that election officials use a variety of technological, physical, and procedural controls to mitigate the likelihood of malicious cyber activity (e.g., phishing, ransomware, denial of service, or domain spoofing) affecting the confidentiality, integrity, or availability of election infrastructure systems or data that would alter votes or otherwise disrupt or prevent voting. These include failsafe measures, such as provisional ballots and backup pollbooks, and safeguards that protect against voting malfunctions (e.g., logic and accuracy testing, chain of custody procedures, paper ballots, and post-election audits). Given the extensive safeguards in place and distributed nature of election infrastructure, the FBI and CISA continue to assess that attempts to manipulate votes at scale would be difficult to conduct undetected.
The public should be aware that election officials use a variety of technological, physical, and procedural controls to mitigate the likelihood of malicious cyber activity (e.g., phishing, ransomware, denial of service, or domain spoofing) affecting the confidentiality, integrity, or availability of election infrastructure systems or data that would alter votes or otherwise disrupt or prevent voting. These include failsafe measures, such as provisional ballots and backup pollbooks, and safeguards that protect against voting malfunctions (e.g., logic and accuracy testing, chain of custody procedures, paper ballots, and post-election audits). Given the extensive safeguards in place and distributed nature of election infrastructure, the FBI and CISA continue to assess that attempts to manipulate votes at scale would be difficult to conduct undetected.
Election systems that house voter registration information or manage non- voting election processes continue to be a target of interest for malicious threat actors. Cyber actors may also seek to spread or amplify false or exaggerated claims of cybersecurity compromises to election infrastructure; however, these attempts would not prevent voting or the accurate reporting of results.a
The FBI and CISA will continue to quickly respond to any potential threats, provide recommendations to harden election infrastructure, notify stakeholders of threats and intrusion activity, and impose risks and consequences on cyber actors seeking to threaten U.S. elections.
Recommendations
- For information about registering to vote, polling locations, voting by mail, provisional ballot process, and final election results, rely on state and local government election officials.
- Remain alert to election-related schemes which may attempt to impede election administration.
- Be wary of emails or phone calls from unfamiliar email addresses or phone numbers that make suspicious claims about the elections process or of social media posts that appear to spread inconsistent information about election-related incidents or results.
- Do not communicate with unsolicited email senders, open attachments from unknown individuals, or provide personal information via email without confirming the requester’s identity. Be aware that many emails requesting your personal information often appear to be legitimate.
- Verify through multiple, reliable sources any reports about compromises of voter information or voting systems, and consider searching for other reliable sources before sharing such information via social media or other avenues.
- Be cautious with websites not affiliated with local or state government that solicit voting information, like voter registration information. Websites that end in “.gov” or websites you know are affiliated with your state or local election office are usually trustworthy. Be sure to know what your state and local elections office websites are in advance to avoid inadvertently providing your information to nefarious websites or actors.
- Report potential crimes—such as cyber targeting of voting systems—to your local FBI Field Office.
- Report cyber-related incidents on election infrastructure to your local election officials and CISA ([email protected]).
 October 4, 2022 — A new report released by Sen. Elizabeth Warren (D-MA) has found reports of scams and fraud on the bank-owned P2P payment network Zelle are surging, but banks have refused to refund customers for most of their losses, even in the face of federal consumer protection law.
October 4, 2022 — A new report released by Sen. Elizabeth Warren (D-MA) has found reports of scams and fraud on the bank-owned P2P payment network Zelle are surging, but banks have refused to refund customers for most of their losses, even in the face of federal consumer protection law.
The report comes at the same time CUToday.info has been reporting on lawsuits filed against financial institutions, including some credit unions, over fraud on the Zelle platform.
The Zelle money transfer system is run by Early Warning, a consortium based in Scottsdale, Ariz., that is owned by seven banks: Bank of America, Capital One, JPMorgan Chase, PNC, Truist, U.S. Bank and Wells Fargo.
Warren said the findings are based on data reported by several of the banks that run the Zelle network, which found the four banks that provided data are on pace to exceed $255 million in fraud on Zelle this year, up from $90 million in 2020, according to the report.
Zelle “is rampant with fraud and theft, and few customers are getting refunded,” said Warren, who sits on the Senate’s Banking Committee.
Acrimonious Hearing
The New York Times noted the report follows a Senate hearing last month that turned acrimonious when Warren pressed the leaders of several large banks about their lack of response to her requests for information about Zelle fraud.
“You didn’t provide any of the information that we requested in our letter, none of it,” Warren said at the hearing. “So, what I want to know is, is that because you don’t keep track when your customers report fraudulent Zelle transactions? Or is it because you do keep track and you know exactly how many fraudulent transactions have been reported, and you want to keep that report a secret?”
Four banks — Bank of America, PNC Bank, U.S. Bank and Truist — provided the data on which Warren’s report was based.
Wide Variations
According to the report, that data revealed wide variations in how the banks addressed fraud claims. PNC refunded only 14% of the 10,683 claims it received about unauthorized Zelle payments, while Truist repaid 82% of its 24,752 claims.
In response to the Warren report, Early Warning responded with a statement that said, “The proportion of fraud and scams has steadily decreased” on its network since its launch in 2017.
In 2021, the company said people sent $490 billion through Zelle (compared with $230 billion through Venmo, its closest rival), a 60% increase from the $307 billion sent in 2020.
Bankers’ Group Responds
Meanwhile, in response to the Warren report, Independent Community Bankers of America President and CEO Rebeca Romero Rainey said,
“ICBA and the nation’s community banks are outraged by increasingly sophisticated fraud perpetrated by criminals against consumers, including those duped into authorizing payments to scammers using Zelle and other peer-to-peer payments services.
“With more than 99.9% of Zelle transactions sent without any report of fraud or scams, community banks appreciate the ability to offer the quick and efficient payments services that customers demand while encouraging Zelle and the largest banks to take measures that improve consumer awareness and protections against fraud. Consumer protection is ingrained in the community bank business model…
“Regulatory restrictions are not the answer to P2P fraud because they will never keep up with the pace of evolving fraud and will serve to disrupt banking services, forcing consumers to look to nonbank money transmission services that operate outside of the banking sector,” Romero Rainey continued. “Further, unlimited liability for P2P fraud under Regulation E would have a disproportionate impact on community banks.
“Instead, policymakers should focus more on the fraudsters and work with P2P technology vendors to maximize consumer awareness of fraud schemes and implement safeguards, such as multifactor authentication, to reduce consumer approvals of fraudulent transactions without delaying consumer access to their funds.”